Security Scanning Tools Overview
There are significant changes happening in the world of software development. How we create applications (monolithic to microservices), how fast we ship them (continuous integration), how much third-party code we bring in (supply chain). Add to this the explosion in the number of software developers, the increase in the number of vulnerabilities, and the ease with which one can exploit these vulnerabilities, and the need for a tight application security/product security initiative is paramount.
Application security (AppSec) is complex. The cycle of development for most software teams typically looks like this:
Devs write code –> they also bring in third-party code –> code is built and artifacts are produced –> builds are deployed in dev/test/stage/prod
For a tight AppSec program, we need to detect vulnerabilities in static artifacts as well as running applications. We also need to prioritize them based on true risk to the application. From a tooling perspective, let’s divide them into two groups: static scanners and runtime scanners.
This article provides a simple glossary for what each of these tools is and does.
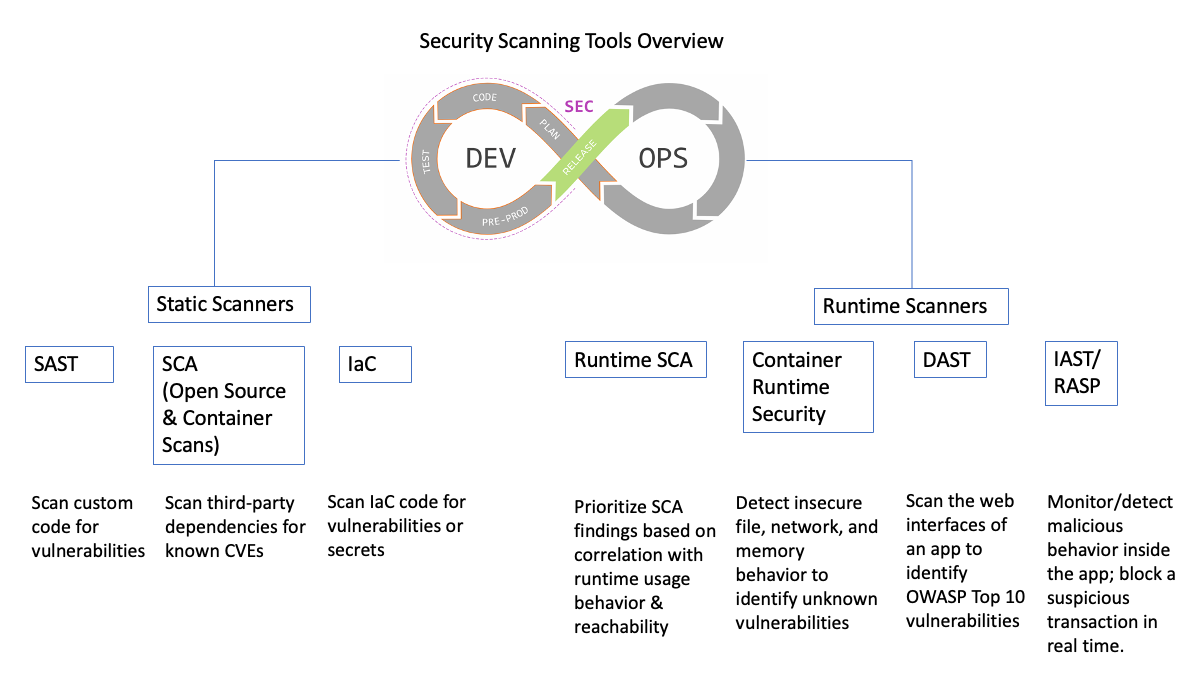
What Are Static Scanners?
These are tools that scan and detect vulnerabilities in static artifacts such as code, builds, and container images. SAST, IaC, SCA (open source and container Scans) fall under this group.
- SAST (Static Application Security Testing): SAST tools scan the source code for the application and determine vulnerabilities or secrets (based on a set of rules that define the errors in the source code that need to be addressed and assessed.). They are typically used to scan custom software written in languages like Java, Python, Node.js, C/C++, etc.
- IaC Scanning (Infrastructure as Code): IaC scanning tools are used to scan IaC code and determine vulnerabilities or secrets. They typically are used to scan scripts written in Terraform, etc.
- SCA (Software Composition Analysis): SCA tools scan code as well as build artifacts such as container images. They determine vulnerabilities in third-party open-source components used by an application or container image. Vulnerabilities are determined based on a comparison with the database of known CVEs. There are several CVE databases in the industry, ranging from free to proprietary, that these tools check against.
Static scanners are typically the first ones to be used in an AppSec program. They are generally quite “noisy” (they produce a lot of alerts and false positives), so it’s important to spend time agreeing on a framework to prioritize these vulnerabilities. For developers to create secure software faster, these tools are often embedded into CI pipelines and developers are notified of vulnerabilities at the time of submission of pull requests and/or builds. Some organizations set up gates to block commits/builds if new critical vulnerabilities get introduced.
What Are Runtime Scanners?
Runtime scanners are tools that scan running applications and detect vulnerabilities as well as correlate feedback to the static scanners. DAST, IAST/RASP, Container Runtime Security and Runtime SCA fall under this group.
- Runtime SCA: This is an emerging category that is highly effective in prioritizing SCA (OSS dependency and container scan ) results based on true risk to the application. Current generation SCA scan results are typically quite noisy and result in a large number of vulnerabilities. But due to the nature of software development, it’s common for many dependencies or OS packages in container images to be bundled with application artifacts but not actually called/reached/used/internet accessible—not actually used. Runtime SCA is a highly effective way to watch the running processes and identify which vulnerable components are actually reached/used/internet accessible etc, and therefore prioritize SCA results based on true risk. This not only helps with prioritization, but also with removal of unused components from the application, burning CVE debt down faster. Runtime SCA tools are a great way to augment SCA tooling and increase developer acceptance of SCA initiatives.
- Container Runtime Security: For more modern applications that are container based, there is a wide variety of attacks that leverage insecure file/network/memory/process behaviors. Container runtime security tools observe application behavior and detect insecure behaviors, ranging from network activity, filesystem activity, and memory behaviors such as buffer overflows, to insecure process behaviors such as privilege escalation. Given the wide variety of application deployment types (self-managed Kubernetes, managed Kubernetes like AWS Fargate, Docker Swarm, AWS Lambda with containers, etc.), it’s important that these tools support them. While AppSec teams use these tools to detect vulnerable behaviors in pre-production environments, it’s more common for these tools to be used by the Ops/SRE teams for SOC2 and other compliance reasons in production environments.
- DAST (Dynamic Application Security Testing): DAST is used to scan the web interfaces of an application to primarily identify OWASP Top 10 vulnerabilities. The DAST scanner treats the application like a black box. It sends HTTP requests to the application’s web interfaces and receives responses. Based on this, it identifies vulnerabilities such as SQLi, and reports this to the user.
- IAST (Interactive Application Security Testing) & RASP (Real-Time Application Self Protection): IAST tools instrument the application from the inside and determine whether a certain vulnerable behavior was exhibited by the application. They examine the HTTP request/response activity demonstrated by the application by observing the application process using language agents such as Java Virtual Machine Tool Interface (JVM TI) or Java agent. Just like DAST, IAST tools also generally detect OWASP Top 10 type vulnerabilities like SQLi. Because IAST tools are observing inside the application process, they can not only detect malicious behavior, but also provide evidence information (such as stack traces) that can help the developer identify root cause and remediate the issue. IAST tools are specific to the language they observe. They don’t send any HTTP requests to the application, and therefore require the user to exercise the application by either running automated tests against it OR by running a DAST scan against it. RASP is essentially IAST running in blocking mode. While IAST can monitor/detect malicious behavior, RASP can block a suspicious transaction in real time.
What Deepfactor Offers
Deepfactor is a new approach to AppSec that combines many of the tools mentioned above—including SCA, container runtime security, runtime SCA, as well as SBOM—into a powerful, easy-to-use, integrated platform. With Deepfactor, you can now correlate static scans with runtime analysis, and prioritize vulnerabilities based on true usage. To see more on the security scanning use cases Deepfactor addresses, you can watch this 5-minute video.
Frequently Asked Questions
1. What are static scanners, and how do they contribute to application security?
Answer: Static scanners are tools that scan and detect vulnerabilities in static artifacts such as code, builds, and container images. They include SAST (Static Application Security Testing), IaC scanning (Infrastructure as Code), and SCA (Software Composition Analysis). SAST tools scan source code for vulnerabilities, IaC scanning tools analyze Infrastructure as Code scripts, and SCA tools detect vulnerabilities in third-party open-source components.
2. How are static scanners integrated into the development process, and what challenges do they pose?
Answer: Static scanners are often embedded into CI pipelines to notify developers of vulnerabilities at the time of code submission or build. However, they can be noisy, producing a high number of alerts and false positives. Prioritizing these vulnerabilities is essential, and some organizations set up gates to block commits or builds with critical vulnerabilities.
3. What are runtime scanners, and how do they complement static scanners?
Answer: Runtime scanners scan running applications to detect vulnerabilities and provide feedback to static scanners. They include Runtime SCA (Software Composition Analysis), Container Runtime Security, DAST (Dynamic Application Security Testing), and IAST/RASP (Interactive Application Security Testing/Real-Time Application Self Protection). Runtime SCA prioritizes vulnerabilities based on true risk by monitoring the usage of vulnerable components in running processes.
4. How does Deepfactor differentiate itself in the field of application security tools?
Answer: Deepfactor combines various security scanning tools, including SCA, container runtime security, runtime SCA, and SBOM (Software Bill Of Materials), into an integrated platform. It correlates static scans with runtime analysis to prioritize vulnerabilities based on actual usage, providing developers with a comprehensive approach to application security.
Free Trial Signup
Deepfactor SaaS includes the full functionality of the Deepfactor Developer Security platform hosted in a multi-tenant environment.