Countless data breaches are exposed daily, and finding the vulnerabilities that are leading to these breaches is extremely important. Businesses have been reliant on open-source components to accelerate their application development, but this convenience does come with a price: the high risk of vulnerabilities associated with said components. This is where the new approach to software composition analysis —“SCA 2.0”— steps in and plays a crucial role in securing modern applications built on open source. The Synopsys OSSRA Report found that 50% of applications have high-risk vulnerabilities, and 90% of applications have at least one open-source component that has not been updated in over two years. These statistics highlight the fact that businesses are sacrificing application security for development speed. With SCA 2.0, there doesn’t have to be this tradeoff; both speed and security can be accomplished.
Limitations of First-Gen SCA
SCA 1.0 tools played a vital role in identifying vulnerabilities in open-source software, but imposed limitations across the organization. These tools generated excessive noise which made the jobs of development teams far more difficult. Finding the severity of a vulnerability is only half the battle; finding how that vulnerability is affecting the application as a whole is equally as important. This led to inefficiencies in development, as developers spent time addressing less critical issues.

For AppSec teams, relying solely on the severity of vulnerabilities could lead to miscommunication between engineering and application security teams. AppSec teams also found themselves manually sifting through vulnerabilities to prioritize them, which is a very time-consuming process. And, leadership was forced to rely solely on vulnerability counts rather than which ones present true risk to the business, seriously hindering the ability to respond to events such as zero-day threats.
Framework for SCA 2.0
The new SCA 2.0 approach provides a more accurate and efficient way to prioritize vulnerabilities. It involves six key parameters for prioritization, going beyond just severity. These additional parameters include runtime usage, reachability, exploit availability, application topology, and applicability of the CVE.
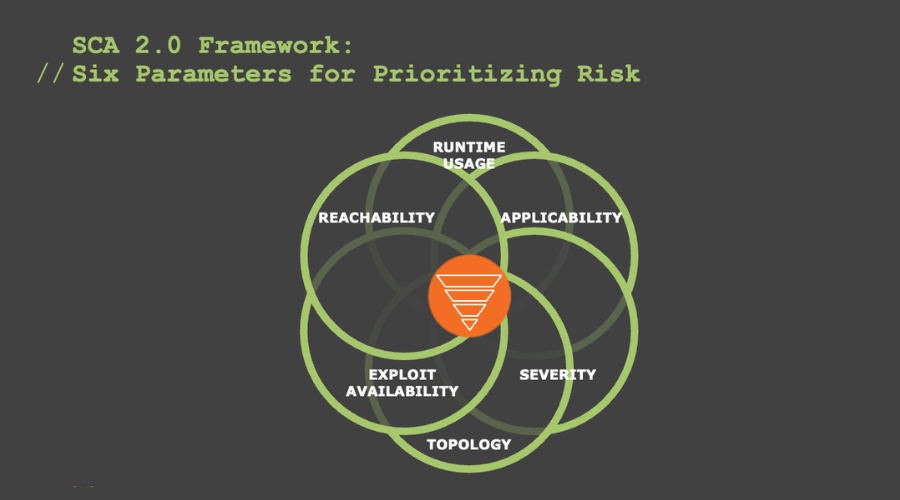
This new approach stems from runtime usage; vulnerabilities in components that are actually being used and reachable at runtime, and exploitable, represent a higher risk and should be addressed first. By using this approach, engineering teams have far more guidance in fixing issues than they would have if they were to go in blind. SCA 2.0 helps distinguish between vulnerabilities that can and should be reached, based on true risk to the business.
The Deepfactor Approach to SCA 2.0
Deepfactor accomplishes this new approach to SCA by not only scanning source code and container images in the CI pipeline, but also dropping into running environments, and providing visibility into the actual behavior of applications, going beyond the limitations of traditional SCA tools. The emphasis on runtime usage as a prioritization metric is a game-changer, enabling organizations to focus their efforts on vulnerabilities that pose a real and immediate threat. The correlation between static scans and runtime observations is presented in a user-friendly interface, complete with a Venn diagram, offering a clear and actionable view of an application’s security posture.
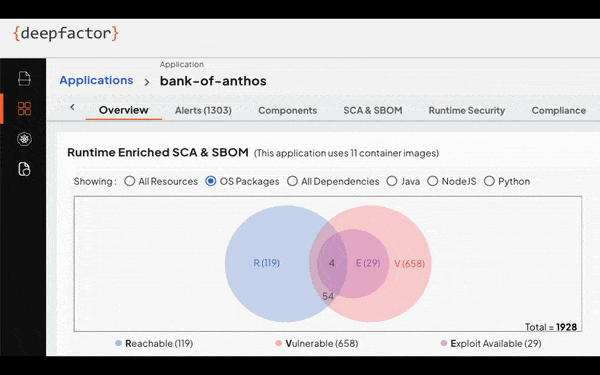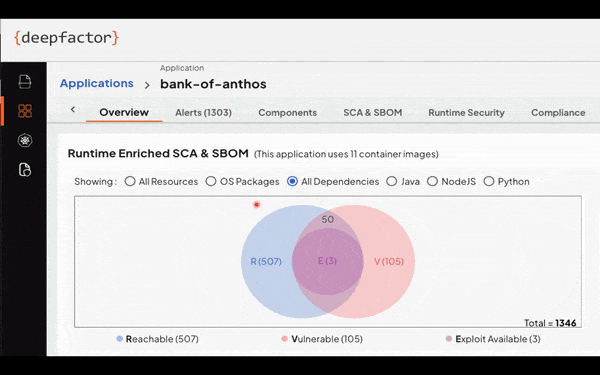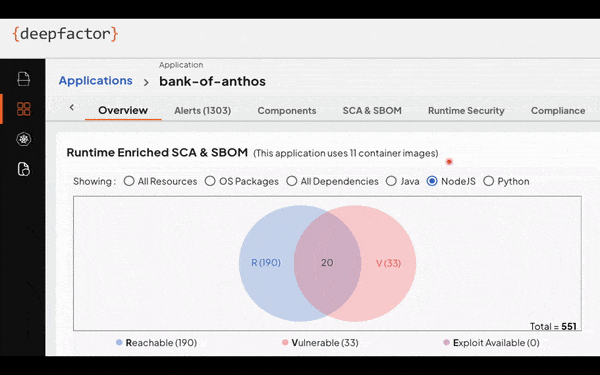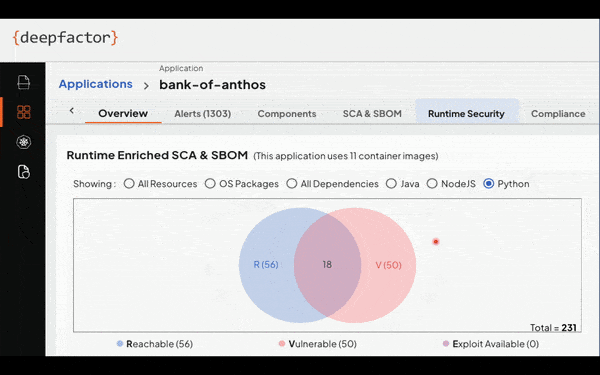
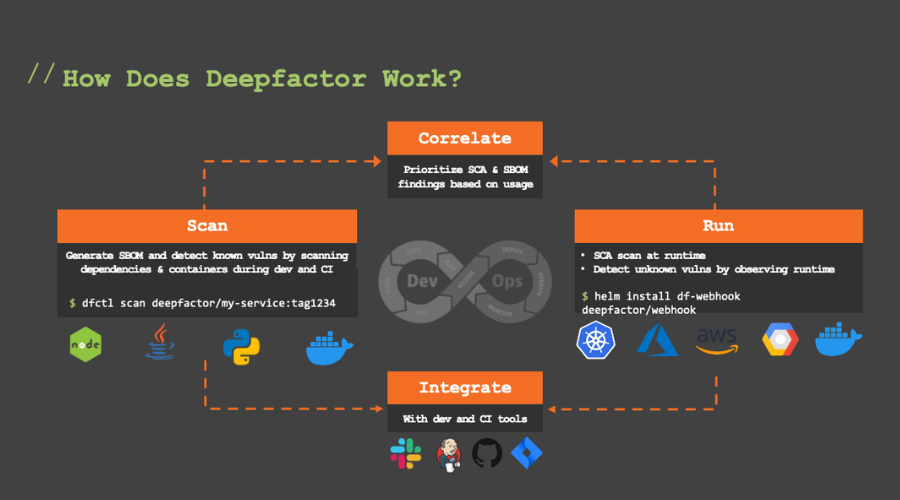
How Does Deepfactor Work?
On the static side, Deepfactor, like traditional SCA tools, scans artifacts and container images during the CI pipeline phase, identifying vulnerabilities and generating essential information such as Software Bill of Materials (SBOMs). On the right side, the Deepfactor platform observes processes and threads within applications at runtime. Simultaneously, Deepfactor analyzes over 200 types of behaviors across file, network, memory processes, and more, detecting anomalous behavior and categorizing misbehaviors. By correlating static scan results with real-time runtime observations, Deepfactor provides a prioritized view of vulnerabilities based on the six key parameters for prioritizing risk as mentioned above.
This hybrid approach of combining static and runtime analysis and correlation empowers organizations to proactively secure their applications by prioritizing and addressing the most critical vulnerabilities first, which significantly streamlines application security processes.
How SCA 2.0 Benefits Your Organization
Deepfactor integrates with various development and operations tools, making it a flexible and powerful addition to any organization’s security arsenal. The Deepfactor Platform brings many practical benefits to organizations navigating modern software development and security. By integrating static and runtime analyses, Deepfactor provides a more comprehensive understanding of vulnerabilities, allowing development teams to prioritize and address the most pressing issues that impose the highest risk to the enterprise. Deepfactor also points out which containers are not being used, so they can be removed, limiting access points into the application. This enhances the security of applications by honing in on vulnerabilities with tangible business risks. Deepfactor’s compatibility with existing development and operations tools fosters a collaborative environment. Its flexibility in deployment, whether standalone or alongside other SCA tools, ensures a seamless fit into diverse organizational infrastructures. Ultimately, organizations adopting Deepfactor can proactively fortify their software applications, minimizing security risks.

Conclusion
In a world where data breaches make headlines daily, the spotlight on software vulnerabilities has never been brighter. Businesses, in their quest for rapid application development, have heavily relied on open-source components. The limitations of the earlier SCA 1.0 era, marked by noise and a lack of holistic visibility, laid the groundwork for a more complete approach. SCA 2.0 introduces a new balance, prioritizing static and runtime usage and addressing vulnerabilities based on real-world impact. As organizations embrace both SCA 2.0 and the Deepfactor platform, they are not just checking security boxes; they are elevating their practices to build a more secure, efficient, and collaborative software development journey.
Frequently Asked Questions
1. What are the limitations of traditional SCA (Software Composition Analysis) tools, and how does SCA 2.0 address these limitations?
Answer: Traditional SCA tools, referred to as SCA 1.0, often generated excessive noise and lacked holistic visibility, making it challenging for development teams to prioritize vulnerabilities effectively. SCA 2.0 introduces a new approach that goes beyond severity, considering parameters like runtime usage, reachability, exploit availability, application topology, and CVE applicability. This approach enables organizations to prioritize vulnerabilities more accurately and efficiently, addressing issues based on their real-world impact.
2. How does Deepfactor differentiate itself in implementing the SCA 2.0 approach compared to traditional SCA tools?
Answer: Deepfactor not only scans artifacts and container images during the CI pipeline phase but also observes processes and threads within applications at runtime. This hybrid approach combines static and runtime analysis, allowing Deepfactor to provide a more comprehensive understanding of vulnerabilities. By correlating static scan results with real-time runtime observations, Deepfactor prioritizes vulnerabilities based on key parameters, empowering organizations to proactively secure their applications and streamline application security processes.
3. What are the practical benefits of adopting the Deepfactor Platform for software development and security?
Answer: The Deepfactor Platform integrates with various development and operations tools, offering flexibility and practical benefits to organizations. By providing a comprehensive understanding of vulnerabilities and prioritizing the most critical issues, Deepfactor enables development teams to fortify their software applications proactively. Additionally, Deepfactor’s compatibility with existing tools and flexible deployment options ensures seamless integration into diverse organizational infrastructures, fostering a collaborative environment and minimizing security risks.
4. How does SCA 2.0, coupled with the Deepfactor Platform, help organizations strike a balance between speed and security in application development?
Answer: SCA 2.0, along with the Deepfactor Platform, enables organizations to address vulnerabilities based on their real-world impact, striking a balance between speed and security in application development. By prioritizing vulnerabilities more accurately and efficiently, development teams can focus their efforts on addressing issues that pose the highest risk to the enterprise, minimizing security risks without compromising development speed. This holistic approach elevates software development practices, making them more secure, efficient, and collaborative.
Free Trial Signup
The Deepfactor trial includes the full functionality of the Deepfactor platform, hosted in a multi-tenant environment.
Sign Up Today! >






