Deepfactor is a developer security platform that enables engineering teams to observe unexpected and risky application behavior during software development, helping developers quickly discover and resolve security vulnerabilities, supply chain risks, and compliance violations. Understanding the value of this information is something we discussed at length in our whitepaper, Observing Application Behavior via API Interception:
“From guaranteeing the workload is performant and stable, to certifying functionality and security hardening, today’s developers require robust runtime analysis to ensure applications are behaving as designed. With careful investigation of the application’s behavior, engineering teams can confidently—and quickly—move from development, through testing, into production.”
However, there’s something we didn’t review in our whitepaper—what exactly is Deepfactor observing to provide engineering teams with the requisite information to remediate security issues before release? And how can that information be customized and refined based on the developer’s area of expertise and focus? Obviously, answering these questions is fundamental to highlighting the uniqueness behind the Deepfactor platform …
… which is the exact goal behind my new blog series entitled, DeepInsights: Understanding and Observing Risky Application Behavior with Deepfactor!
Introducing DeepInsights
Join me—Mike Larkin, Deepfactor CTO— each month as we review the rapidly growing stable of insights available in Deepfactor. Our objective is to highlight the wealth of information we’ve made available to developers hoping to triage and remediate security risks early in the Software Development Life Cycle (SDLC). Our blog series will center around the following categories:
- Behavior Violations
- System Call / Library Call Risks
- Vulnerable Operating Systems or Operating System Packages
- Vulnerable Application Dependencies (e.g. 3rd party libraries)
- Vulnerable Web APIs (e.g. XSS, SQLI, etc.)
However, before jumping into our first set of alerts, it’s worth discussing how developers can customize and manage alerts in Deepfactor.
What are Alert Policies?
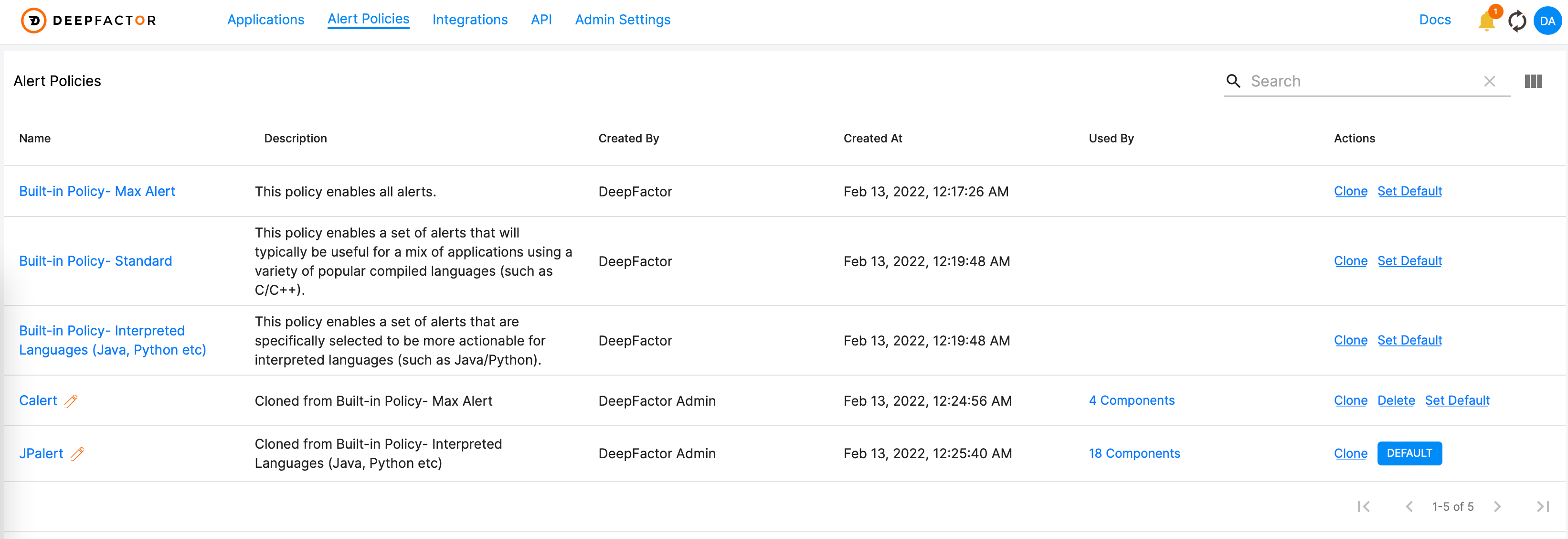
Our portal analyzes telemetry (i.e. event data) received from running applications and generates alerts based on the Alert Policy defined during instrumentation. Though there are several built-in policies (e.g. Standard and Max Alert), developers are encouraged to create net-new—or even clone existing—policies to meet specific application security requirements. And once created, Alert Polices can track which applications are being observed and users can configure them as default when deploying new workloads. (Figure 1)
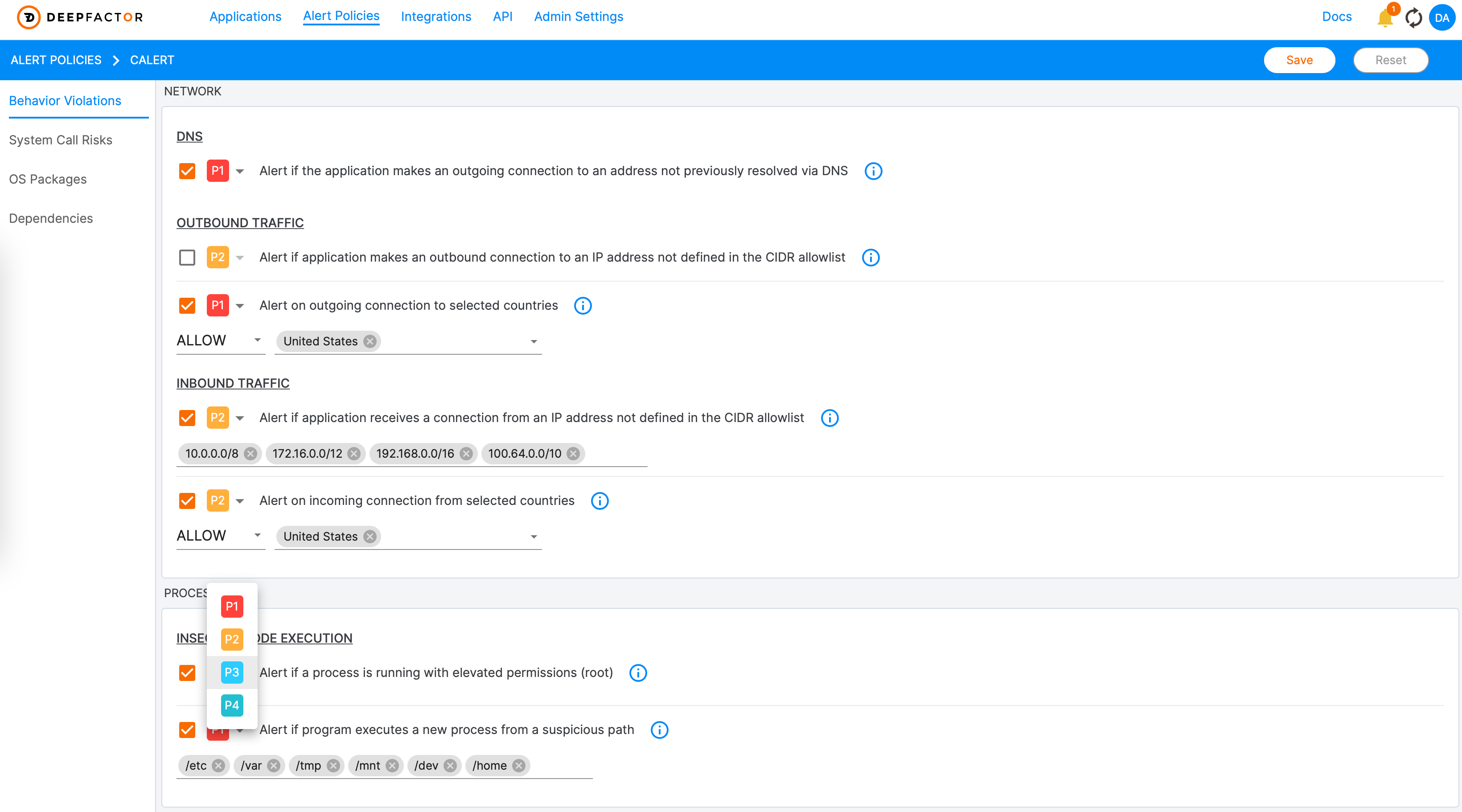
Once created, users can enable/disable specific alerts, configure trigger criteria (e.g. “Alert on outgoing connection to select countries—Russia, North Korea, etc.”), and set the default priority. This flexibility enables developers to curate the metrics and rules used to generate alerts from incoming telemetry. (Figure 2)
Join Me Next Week for Behavior Violations
Obviously, creating and configuring Alert Policies in Deepfactor is integral to the developer experience—hence my excitement for the upcoming blog series, DeepInsights. I hope we can provide you with a deeper understanding of what Deepfactor is observing to provide developers with contextual, application-aware security insights.
In our first series of blogs, we’re going to focus on Behavior Violations. Behavior Violations are divided into 4 sub-categories —Network Violations, Process Violations, Library Related Violations and Node (i.e. Environmental) Violations. Join me over the coming weeks as I focus on one sub-category in each blog, providing you with descriptions, trigger criteria, and real-world examples for each alert. The goal is to educate you on why these alerts are important, highlighting why we chose to focus on them in the first place!
In the meantime, consider reviewing the following resources for additional education information:
- Observing Application Behavior via API Interception [Whitepaper]
- What is the best way to observe application behavior at runtime? [Blog]
- Alert Policies [Documentation]
Looking forward to continuing this blog series!