Find out answers and explanations to the weekly Deepfactor Deep Hacks! We are drawing from the experience of our community of security and dev professionals to provide you with helpful tips and things to watch out for as you’re creating secure cloud native apps.
Click to expand each weekly hack below for answers and explanations.
-
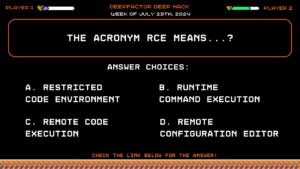
Deep Hack of the week July 29th, 2024: The acronym RCE means...?
Question:
The acronym RCE means…?
Answer Choices:
a) Restricted Code Environment
b) Runtime Command Execution
c) Remote Code Execution
d) Remote Configuration Editor
Correct Answer:
c) Remote Code Execution
Explanation:
The correct answer is c) Remote Code Execution because RCE refers to a critical security vulnerability where an attacker can execute arbitrary code on a remote machine or system without physical access. This type of vulnerability is extremely dangerous as it allows the attacker to gain control over the affected system, potentially leading to unauthorized access, data breaches, and further exploitation within the network. RCE is a top concern in application security due to its severe impact and potential for widespread damage.
-
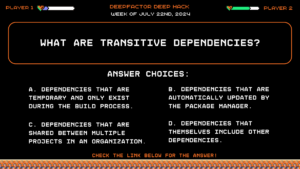
Deep Hack of the week July 22nd, 2024: What are transitive dependencies?
Question:
What are transitive dependencies?
Answer Choices:
a) Dependencies that are temporary and only exist during the build process.
b) Dependencies that are automatically updated by the package manager.
c) Dependencies that are shared between multiple projects in an organization.
d) Dependencies that themselves include other dependencies.
Correct Answer:
d) Dependencies that themselves include other dependencies.
Explanation:
-
Deep Hack of the week July 15th, 2024: SBOMs can be represented in several common formats (Select all Correct Answers).
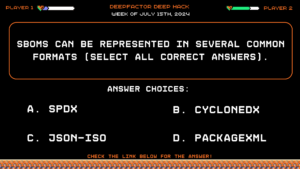
Question:
SBOMs can be represented in several common formats (Select all Correct Answers).
Answer Choices:
a) SPDX
b) CycloneDX
c) JSON-ISO
d) PackageXML
Correct Answer:
a) SPDX and b) CycloneDX
Explanation:
-
Deep Hack of the week July 8th, 2024: An XSS vulnerability can result in which type of exploit?
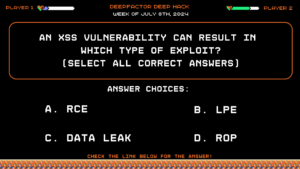
Question:
An XSS vulnerability can result in which type of exploit? (Select all correct answers)
Answer Choices:
a) RCE
b) LPE
c) Data Leak
d) ROP
Correct Answer:
a) RCE and c) Data Leak
Explanation:
-
Deep Hack of the week June 24th, 2024: If you have bug free code, then by definition you also have secure code.

Question:
If you have bug free code, then by definition you also have secure code.
Answer Choices:
True
False
Correct Answer:
False
Explanation:
-
Deep Hack of the week June 17th, 2024: What is the purpose of a CVE? (What are CVEs used for?)
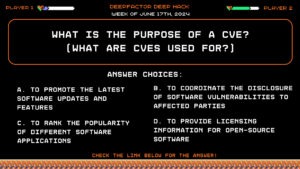
Question:
What is the purpose of a CVE? (What are CVEs used for?)
Answer Choices:
a) To promote the latest software updates and features
b) To coordinate the disclosure of software vulnerabilities to affected parties
c) To rank the popularity of different software applications
d) To provide licensing information for open-source software
Correct Answer:
b) To coordinate the disclosure of software vulnerabilities to affected parties
Explanation:
CVE (Common Vulnerabilities and Exposures) provides a standardized way to identify and share information about software vulnerabilities. The main purpose of CVEs is to ensure that vulnerabilities are consistently referenced and disclosed to affected parties, such as software vendors and users, enabling them to quickly address and mitigate the risks. This coordination helps in maintaining security across various systems and platforms by facilitating timely patches and security updates.
-
Deep Hack of the Week June 10th, 2024: SCA tools are limited to scanning container images.
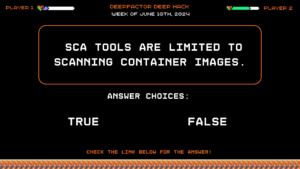
Question:
SCA tools are limited to scanning container images.
Answer Choices:
True
False
Correct Answer:
False
Explanation:
SCA (Software Composition Analysis) tools are not limited to scanning container images. They are designed to analyze and manage the open-source components and libraries used in software applications. SCA tools can scan source code, binaries, and dependencies to identify vulnerabilities, license compliance issues, and outdated components across various environments, including but not limited to container images. If you want more information on SCA, check out our whitepaper here.
-
Deep Hack of the Week May 27th, 2024: Memory safety bugs account for what percentage of issued CVEs?
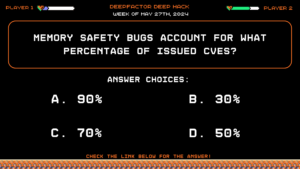
Question:
Memory safety bugs account for what percentage of issued CVEs?Answer Choices:
a) 90%
b) 50%
c) 70%
d) 30%
Correct Answer:
c) 70%
Explanation:
Memory safety bugs, such as buffer overflows and use-after-free errors, account for 70% of issued CVEs (Common Vulnerabilities and Exposures) due to their high prevalence and severe impact on software security. These vulnerabilities occur when a program mismanages memory operations, leading to potential security risks like arbitrary code execution. Historical data and reports from organizations such as MITRE consistently show that a significant portion of CVEs are related to memory safety issues. Their dangerous nature, often allowing remote exploitation and system control, highlights the critical need for robust memory management and security measures in software development.
-
Deep Hack of the Week May 20th, 2024: What are the two main types of vulnerability reachability analysis techniques?
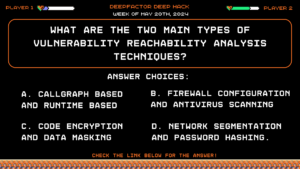
Question:
What are the two main types of vulnerability reachability analysis techniques?Answer Choices:
a) Call Graph Based and Runtime Based
b) Firewall configuration and antivirus scanning
c) Code encryption and data masking
d) Network segmentation and password hashing.
Correct Answer:
a) Call Graph Based and Runtime Based
Explanation:
The two main types of vulnerability reachability analysis techniques are Call Graph Based and Runtime Based. Call Graph Based analysis involves creating a call graph to represent the calling relationships between different functions or methods in the code, allowing for the identification of which parts of the code can be reached and potentially exploited by an attacker. Runtime Based analysis, on the other hand, involves monitoring the program during its execution to observe which parts of the code are actually executed. This method captures dynamic behavior and interactions that occur only during execution, providing a comprehensive view of potential vulnerabilities. Other methods such as firewall configuration, antivirus scanning, code encryption, data masking, network segmentation, and password hashing are not related to vulnerability reachability analysis, but rather are security measures for protecting systems and data.
-
Deep Hack of the Week May 13th, 2024: What CPU hardware capabilities can be used to mitigate the danger of CFI attacks?
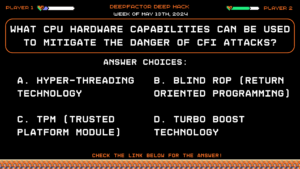
Question:
What CPU hardware capabilities can be used to mitigate the danger of CFI attacks?Answer Choices:
a) Hyper-Threading Technology
b) Blind ROP (Return Oriented Programming)
c) TPM (Trusted Platform Module)
d) Turbo Boost Technology
Correct Answer: b) Blind ROP (Return Oriented Programming)
Explanation:
Answer A (Hyper-Threading Technology) improves parallelism by allowing multiple threads to run on each CPU core but does not provide direct support for mitigating CFI attacks. Answer C (TPM (Trusted Platform Module)) provides hardware-based security functions, such as secure key storage and cryptographic operations, but it is not designed specifically to mitigate CFI attacks within the CPU execution flow. Answer D (Turbo Boost Technology) enhances CPU performance by increasing clock speed dynamically based on workload but is unrelated to control flow integrity mechanisms. Therefore, B (Blind ROP) is the best answer due to what CFI attacks actually attack.
-
Deep Hack of the Week April 29th, 2024: Which of the following is one of the activities at Deepfactor’s pod at AppSec Village next Wednesday, May 8th?
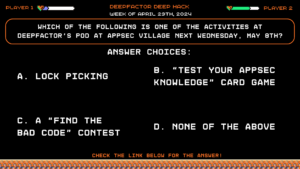
Question:
Which of the following is one of the activities at Deepfactor’s pod at AppSec Village next Wednesday, May 8th?Answer Choices:
a) Lock picking
b) “Test your Appsec knowledge” card game
c) A “find the bad code” contest
d) None of the above
Correct Answer: b) “Test your Appsec knowledge” card game
Explanation:
Check out our Pod at AppSec Village on Wednesday, May 8th to play our brand new “Test Your AppSec Knowledge” card game! Check this link for sign-ups and more information. See you there!
-
Deep Hack of the Week April 22nd, 2024: Which of the following best describes the term "Fuzzing" in the context of application security testing?
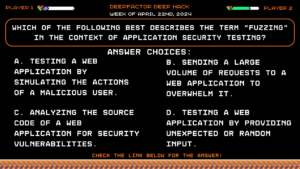
Question:
Which of the following best describes the term “Fuzzing” in the context of application security testing?Answer Choices:
a) Testing a web application by simulating the actions of a malicious user.
b) Sending a large volume of requests to a web application to overwhelm it.
c) Analyzing the source code of a web application for security vulnerabilities.
d) Testing a web application by providing unexpected or random input.
Correct Answer: d) Testing a web application by providing unexpected or random input.
Explanation:
Fuzzing is a technique used in application security testing to find vulnerabilities by providing unexpected or random input to a system and monitoring its behavior for unexpected results. Fuzzing can help identify security vulnerabilities such as buffer overflows, input validation errors, and more.
-
Deep Hack of the Week April 15th, 2024: Which of the following security measures helps prevent Clickjacking attacks by ensuring that a web page cannot be embedded within a frame or iframe?
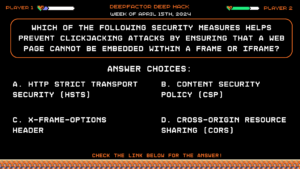
Question:
Which of the following security measures helps prevent Clickjacking attacks by ensuring that a web page cannot be embedded within a frame or iframe?Answer Choices:
a) HTTP Strict Transport Security (HSTS)
b) Content Security Policy (CSP)
c) X-Frame-Options header
d) Cross-Origin Resource Sharing (CORS)
Correct Answer: c) X-Frame-Options header
Explanation:
The X-Frame-Options header allows web developers to control whether a web page can be embedded within a frame or iframe, helping prevent Clickjacking attacks by ensuring that the page cannot be loaded in a malicious context.
-
Deep Hack of the Week April 8th, 2024: Which security mechanism can help prevent man-in-the-middle attacks by verifying the authenticity of a server's digital certificate?

Question:
Which security mechanism can help prevent man-in-the-middle attacks by verifying the authenticity of a server’s digital certificate?Answer Choices:
a) Certificate Revocation Lists (CRLs)
b) Public Key Infrastructure (PKI)
c) Secure Sockets Layer (SSL)
d) Perfect Forward Secrecy (PFS)
Correct Answer: c) Secure Sockets Layer (SSL)
Explanation:
Secure Sockets Layer (SSL) certificates are used to establish a secure and encrypted connection between a client and a server. By verifying the authenticity of the server’s digital certificate, SSL helps prevent man-in-the-middle attacks where an attacker intercepts and modifies communication between the client and server.
-
Deep Hack of the Week April 1st, 2024: How was the XZ backdoor discovered?
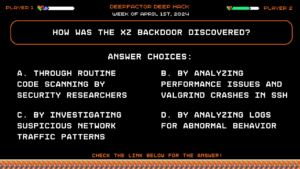
Question:
How was the XZ backdoor discovered?Answer Choices:
a) Through routine code scanning by security researchers
b) By analyzing performance issues and valgrind crashes in ssh
c) By investigating suspicious network traffic patterns
d) By analyzing logs for abnormal behavior
Correct Answer: b) By analyzing performance issues and valgrind crashes in ssh
Explanation:
Andres Freund discovered the backdoor while investigating odd ssh performance issues and valgrind crashes, as mentioned in the blog “XZ backdoor Part 1: An Accidental Discovery of a Backdoor Likely Prevented Thousands of Infections“.
-
Deep Hack of the Week March 18th, 2024: What security mechanism can help protect against Cross-Site Scripting (XSS) attacks by sanitizing and encoding user input before displaying it?
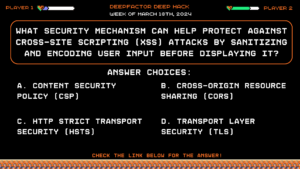
Question:
What security mechanism can help protect against Cross-Site Scripting (XSS) attacks by sanitizing and encoding user input before displaying it?Answer Choices:
a) Content Security Policy (CSP)
b) Cross-Origin Resource Sharing (CORS)
c) HTTP Strict Transport Security (HSTS)
d) Transport Layer Security (TLS)
Correct Answer: a) Content Security Policy (CSP)
Explanation:
Content Security Policy (CSP) allows web developers to mitigate XSS attacks by defining and enforcing a set of content security rules for their web applications. It can help prevent XSS attacks by controlling where resources are loaded from and enforcing proper encoding and sanitization of user input.
-
Deep Hack of the Week March 11th, 2024: Which HTTP method should be used for requests that only retrieve data and do not cause any side effects?
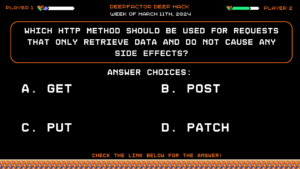
Question:
Which HTTP method should be used for requests that only retrieve data and do not cause any side effects?Answer Choices:
a) GET
b) POST
c) PUT
d) PATCH
Correct Answer: a) GET
Explanation:
The GET method is used for requests that only retrieve data and do not cause any side effects on the server or modify resources. POST, PUT, and PATCH methods are used for requests that may have side effects or modify resources on the server.
-
Deep Hack of the Week March 4th, 2024: Which of the following is a technique to mitigate the risk of SQL Injection attacks?
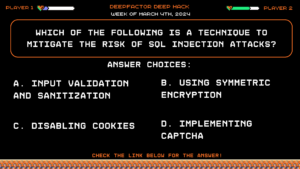
Question:
Which of the following is a technique to mitigate the risk of SQL Injection attacks?Answer Choices:
a) Input validation and sanitization
b) Using symmetric encryption
c) Disabling cookies
d) Implementing CAPTCHA
Correct Answer: a) Input validation and sanitization
Explanation:
Input validation and sanitization involve validating user input and filtering out potentially malicious characters to prevent SQL Injection attacks. The other options listed are not directly related to mitigating SQL Injection vulnerabilities.
-
Deep Hack of the Week February 26th, 2024: What is the purpose of supplemental metrics in CVSS 4.0?
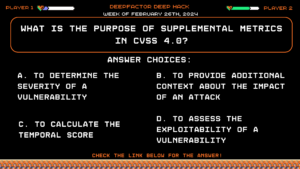
Question:
What is the purpose of supplemental metrics in CVSS 4.0?Answer Choices:
a) To determine the severity of a vulnerability
b) To provide additional context about the impact of an attack
c) To calculate the temporal score
d) To assess the exploitability of a vulnerability
Correct Answer: b) To provide additional context about the impact of an attack
Explanation:
According to episode two of the Next-Gen AppSec series on CVSS 4.0, supplemental metrics in CVSS 4.0 offer additional information about the impact of an attack, enhancing understanding beyond just the severity. If you would like to learn more, check out the full episode here.
-
Deep Hack of the Week February 19th, 2024: What is considered a secret in the context of application security?
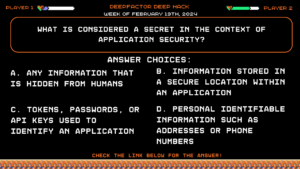
Question:
What is considered a secret in the context of application security?Answer Choices:
a) Any information that is hidden from humans
b) Information stored in a secure location within an application
c) Tokens, passwords, or API keys used to identify an application
d) Personal Identifiable Information such as addresses or phone numbers
Correct Answer: c) Tokens, passwords, or API keys used to identify an application
Explanation:
According to the third episode of the Next-Gen AppSec series on secrets, secrets are defined as tokens, passwords, or API keys used to identify an application. If you want to learn more, check out the full episode here.
-
Deep Hack of the Week February 12th, 2024: You're designing a secure password reset mechanism. Which of the following options offers the strongest resistance to phishing attacks and credential stuffing?
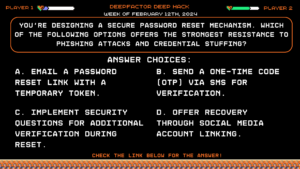
Question:
You’re designing a secure password reset mechanism. Which of the following options offers the strongest resistance to phishing attacks and credential stuffing?Answer Choices:
a) Email a password reset link with a temporary token.
b) Send a one-time code (OTP) via SMS for verification.
c) Implement security questions for additional verification during reset.
d) Offer recovery through social media account linking.
Correct Answer: b) Send a one-time code (OTP) via SMS for verification.
Explanation:
Email links (A) and social media linking (D) are susceptible to phishing attacks. Security questions (C) can be easily guessed or socially engineered. While SMS OTPs (B) provide a stronger layer of security by requiring immediate user interaction, consider alternative secure channels like push notifications or dedicated authenticator apps for even greater phishing resistance.
-
Deep Hack of the Week February 5th, 2024: You're building a serverless application running on a cloud platform. What are the trade-offs between container-based and serverless execution environments in terms of security?
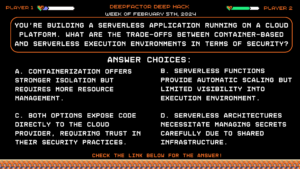
Question:
You’re building a serverless application running on a cloud platform. What are the trade-offs between container-based and serverless execution environments in terms of security?Answer Choices:
a) Containerization offers stronger isolation but requires more resource management.
b) Serverless functions provide automatic scaling but limited visibility into execution environment.
c) Both options expose code directly to the cloud provider, requiring trust in their security practices.
d) Serverless architectures necessitate managing secrets carefully due to shared infrastructure.
Correct Answer: d) Serverless architectures necessitate managing secrets carefully due to shared infrastructure.
Explanation:
While both options (A, B) have their upsides and downsides, the key takeaway is not a single “best choice” but understanding the trade-offs. Consider containerization for stricter isolation and control, but be aware of resource management overhead. Serverless functions offer scalability and reduced operational burden, but lack visibility and require careful secret management due to shared infrastructure (D).
-
Deep Hack of the Week January 29th, 2024: Approximately what percentage of company applications have at least one open-source component that has not been updated in over two years?
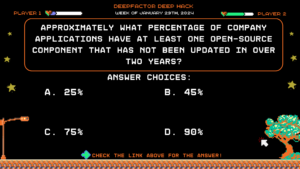
Question:
Approximately what percentage of company applications have at least one open-source component that has not been updated in over two years?
Answer Choices:
a) 25%
b) 45%
c) 75%
d) 90%
Correct Answer: d) 90%
Explanation:
The Synopsys OSSRA report explicitly mentions that 50% of companies have high-risk vulnerabilities, and 90% of applications have at least one open-source component that has not been updated in over two years. If you want to learn more about this report and more, be sure to check out our SCA 2.0 Workshop.
-
Deep Hack of the Week January 22nd, 2024: You're designing a secure API for your application. Which of the following principles should be prioritized for effective API security?
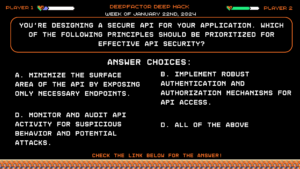
Question:
You’re designing a secure API for your application. Which of the following principles should be prioritized for effective API security?
Answer Choices:
a) Minimize the surface area of the API by exposing only necessary endpoints.
b) Implement robust authentication and authorization mechanisms for API access.
c) Validate all input and output data exchanged through the API.
d) All of the above.
Correct Answer: d) All of the above.
Explanation:
All listed principles (A-C) are crucial for API security. Minimizing exposed endpoints (A) reduces attack vectors. Strong authentication and authorization (B) ensure appropriate access controls. Input and output validation (C) prevents malicious data manipulation. Therefore, prioritizing all aspects (D) is essential for comprehensive API security.
-
Deep Hack of the Week January 8th, 2024: You're implementing secure coding practices in your development process. Which of the following is NOT a best practice for secure coding?
Question:
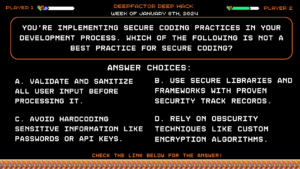
You’re implementing secure coding practices in your development process. Which of the following is NOT a best practice for secure coding?
Answer Choices:
a) Validate and sanitize all user input before processing it.
b) Use secure libraries and frameworks with proven security track records.
c) Avoid hardcoding sensitive information like passwords or API keys.
d) Rely on obscurity techniques like custom encryption algorithms.
Correct Answer: d) Rely on obscurity techniques like custom encryption algorithms.
Explanation:
Obscurity techniques (E) are unreliable and easily bypassed by attackers. Secure coding practices focus on proactive measures like input validation (A), secure libraries (B), and avoiding hardcoding secrets (C).
-
Deep Hack of the Week January 1st, 2024: You're building a new database for your application. What is the PRIMARY purpose of data encryption in this context?
Question:
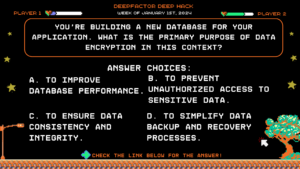
You’re building a new database for your application. What is the PRIMARY purpose of data encryption in this context?
Answer Choices:
a) To improve database performance.
b) To prevent unauthorized access to sensitive data.
c) To ensure data consistency and integrity.
d) To simplify data backup and recovery processes.
Correct Answer: b) To prevent unauthorized access to sensitive data.
Explanation:
While data encryption doesn’t directly improve performance (A), ensure data consistency (C), or simplify backups (D), its primary purpose is to protect sensitive information. Encryption renders the data unreadable without the decryption key, significantly reducing the impact of a data breach.
-
Deep Hack of the Week December 25th, 2023: You're building a web application that allows users to upload and share photos. Which of the following is the MOST effective way to prevent malicious file uploads?
Question:
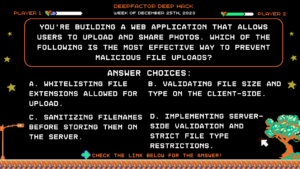
You’re building a web application that allows users to upload and share photos. Which of the following is the MOST effective way to prevent malicious file uploads?
Answer Choices:
a) Whitelisting file extensions allowed for upload.
b) Validating file size and type on the client-side.
c) Sanitizing filenames before storing them on the server.
d) Implementing server-side validation and strict file type restrictions.
Correct Answer: d) Implementing server-side validation and strict file type restrictions.
Explanation:
Client-side validation (A, B) can be bypassed by malicious users manipulating requests. Sanitizing filenames (C) doesn’t address the content within the file. Server-side validation ensures only allowed file types are uploaded and processed, significantly reducing the risk of malicious code execution or data injection.
-
Deep Hack of the Week December 18th, 2023: According to the Synopsys OSSRA Report, what percentage of companies have high risk vulnerabilities?
Question:
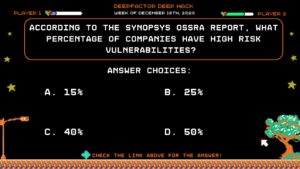
According to the Synopsys OSSRA Report, what percentage of companies have high risk vulnerabilities?
Answer Choices:
a) 15%
b) 25%
c) 40%
d) 50%
Correct Answer: d) 50%
Explanation:
The Synopsys OSSRA report explicitly mentions that 50% of companies have high-risk vulnerabilities, and 90% of applications have at least one open-source component that has not been updated in over two years. If you want to learn more about this report and more, be sure to check out our SCA 2.0 Workshop.
-
Deep Hack of the Week December 4th, 2023: Which of the following is a reason to implement container runtime security?
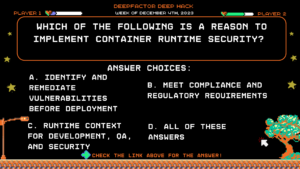
Question:
Which of the following is a reason to implement container runtime security?
Answer Choices:
a) Identify and remediate vulnerabilities before deployment
b) Meet compliance and regulatory requirements
c) Runtime context for development, QA, and security
d) All of these answers
Correct Answer: d) All of these answers
Explanation:
All of these answers are explicitly mentioned in the Container Runtime Security Whitepaper as reasons to implement container runtime security into your applications.
-
Deep Hack of the Week November 27th, 2023: Which of the following is not one of the main SBOM formats?
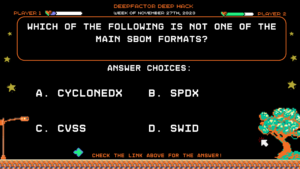
Question:
Which of the following is not one of the main SBOM formats?
Answer Choices:
a) CycloneDX
b) SPDX
c) CVSS
d) SWID
Correct Answer: c) CVSS
Explanation: Option C, CVSS (Common Vulnerability Scoring System), is not mentioned as one of the main SBOM formats in the whitepaper SBOM Security: Top 5 Reasons to Build SBOMs Into Your Pipeline. CVSS is a scoring system used to assess the severity of software vulnerabilities, but it is not a format for representing the complete bill of materials for software components in the supply chain. Therefore, CVSS is the correct answer as it does not fall into the category of the three main SBOM formats explicitly discussed in the whitepaper.
-
Deep Hack of the Week November 13th, 2023: Which of the following is not an API Interception technique?
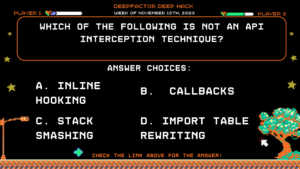
Question:
Which of the following is not an API Interception technique?
Answer Choices:
a) Inline hooking
b) Callbacks
c) Stack smashing
d) Import table rewriting
Correct Answer: c) Stack smashing
Explanation: As published in our whitepaper Observing Application Behavior via API Interception, callbacks, import table rewriting, and inline hooking are all API Interception techniques. However, stack smashing is a technique used in exploiting vulnerabilities by overrunning a buffer on the stack. It is not a typical API Interception technique.
-
Deep Hack of the Week November 6th, 2023: What are the six parameters mentioned for achieving visibility into the risk of an application in SCA 2.0?

Question:
What are the six parameters mentioned for achieving visibility into the risk of an application in SCA 2.0?
Answer Choices:
a) Reachability, runtime usage, applicability, exploit availability, severity, and topology
b) Performance, scalability, security, applicability, exploitability, and topology
c) Applicability, exploitability, topology, security, severity, and usage
d) Security, reachability, usage, availability, exploitability, and topology
Correct Answer: a) Reachability, runtime usage, applicability, exploit availability, severity, and topology
Explanation: As published in our new video “What is SCA 2.0 and What are its Applications,” these six parameters are crucial for achieving visibility into the risk of an application in SCA 2.0.
-
Deep Hack of the Week October 30th, 2023: What is the primary purpose of SBOMs in addressing software supply chain risks?
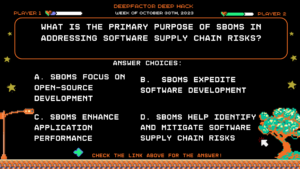
Question:
What is the primary purpose of SBOMs in addressing software supply chain risks?
Answer Choices:
a) SBOMs focus on open-source development
b) SBOMs expedite software development
c) SBOMs enhance application performance
d) SBOMs help identify and mitigate software supply chain risks
Correct Answer: d) SBOMs help identify and mitigate software supply chain risks
Explanation: SBOMs play a crucial role in identifying vulnerabilities, addressing risks, and managing the security and integrity of software supply chains. They provide information about the software components and dependencies, helping organizations prioritize and mitigate potential risks effectively. Option D is the correct answer.
Be sure to check out the SBOMs Whitepaper to learn more!
-
Deep Hack of the Week October 23rd, 2023: Why is container runtime security important during the development and testing phases?
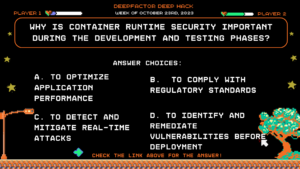
Question:
Why is container runtime security important during the development and testing phases?
Answer Choices:
a) To optimize application performance
b) To comply with regulatory standards
c) To detect and mitigate real-time attacks
d) To identify and remediate vulnerabilities before deployment
Correct Answer: d) To identify and remediate vulnerabilities before deployment
Explanation: Container runtime security during the development and testing phases helps identify and address security flaws before applications are deployed to production, reducing the number of vulnerabilities reaching production.
-
Deep Hack of the Week October 16th, 2023: What is the significance of "reachability" in the SCA 2.0 framework?

Question:
What is the significance of “reachability” in the SCA 2.0 framework?
Answer Choices:
a) It assesses the severity of a vulnerability.
b) It determines if a vulnerable component is being used.
c) It identifies the code paths that can exploit a vulnerability.
d) It measures the difficulty of exploiting a vulnerability.
Correct Answer: c) It identifies the code paths that can exploit a vulnerability.
Explanation: In the context of the SCA 2.0 framework, “reachability” refers to the assessment of how a vulnerability can be exploited. It helps in understanding the specific code paths within an application where a vulnerability, particularly one present in a transitive dependency, can be reached and potentially exploited. By analyzing reachability, SCA tools can pinpoint the pathways that attackers might use to compromise the security of the application. This information is essential for prioritizing remediation efforts and providing guidance to developers on how to address vulnerabilities efficiently.
-
Deep Hack of the Week October 9th, 2023: Why is container runtime security considered crucial during the development and testing phases of cloud-native applications?
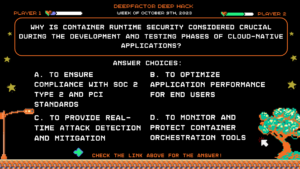
Question:
Why is container runtime security considered crucial during the development and testing phases of cloud-native applications?
Answer Choices:
a) To ensure compliance with SOC 2 Type 2 and PCI standards
b) To optimize application performance for end users
c) To provide real-time attack detection and mitigation
d) To monitor and protect container orchestration tools
Correct Answer: a) To ensure compliance with SOC 2 Type 2 and PCI standards
Explanation: Container runtime security is vital during the development and testing phases to identify and address security risks and ensure compliance with standards like SOC 2 Type 2 and PCI. It is not primarily focused on performance but on security and compliance.
-
Deep Hack of the Week October 2nd, 2023: What security concern is evident in the code snippet below for initiating OAuth 2.0 implicit flow?
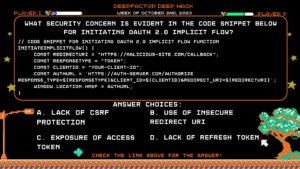
Question:
// Code snippet for initiating OAuth 2.0 Implicit Flow function initiateImplicitFlow() {
const redirectUri = “https://malicious-site.com/callback”;
const responseType = “token”;
const clientId = “your-client-id”;
const authUrl = `https://auth-server.com/authorize
response_type=${responseType}&client_id=${clientId}&redirect_uri=${redirectUri}`;
window.location.href = authUrl;
}Answer Choices:
a) Lack of CSRF Protection
b) Use of Insecure Redirect URI
c) Exposure of Access Token
d) Lack of Refresh Token
Correct Answer: b) Use of Insecure Redirect URI
Explanation: The code uses a malicious redirect URI, which could allow an attacker to steal the access token issued by the authorization server in the Implicit Flow. Remediation: Use only secure and trusted redirect URIs that are registered with your OAuth client. This ensures that the access token is sent back only to valid and authorized locations. Additionally, validate the state parameter to mitigate CSRF attacks.
-
Deep Hack of the Week Spetember 27th, 2023: What vulnerability could be exploited using this Open ID connect (OIDC) callback code?
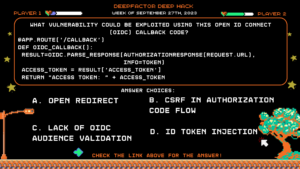
Question:
What vulnerability could be exploited using this Open ID connect (OIDC) callback code?
@app.route(‘/callback’)
def oidc_callback():
result = oidc.parse_response(AuthorizationResponse(request.url), info=token)
access_token = result[‘access_token’]
return “Access Token: ” + access_tokenAnswer Choices:
a) Open Redirect
b) CSRF in Authorization Code Flow
c) Lack of OIDC Audience Validation
d) ID Token Injection
Correct Answer: b) CSRF in Authorization Code Flow
Explanation: The code does not include any state or nonce validation, making it susceptible to Cross-Site Request Forgery (CSRF) attacks in the OIDC flow. State and nonce parameters should always be used to prevent such attacks.
-
Deep Hack of the Week September 11th, 2023: Which vulnerability could this function introduce in the OpenID connect (OIDC) flow?
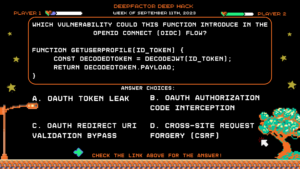
Question:
Which vulnerability could this function introduce in the OpenID connect (OIDC) flow?
function getUserProfile(id_token) {
const decodedToken = decodeJWT(id_token);
return decodedToken.payload;
}
Answer Choices:
a) OAuth Token Leak
b) OAuth Authorization Code Interception
c) OAuth Redirect URI Validation Bypass
d) Cross-Site Request Forgery (CSRF)
Correct Answer: c) OAuth Redirect URI Validation Bypass
Explanation: The code lacks proper validation of the redirect URI, which could be manipulated by an attacker to redirect users to malicious sites after authorization.
-
Deep Hack of the Week September 4th, 2023: Why is the use of a state parameter important in OAuth 2.0 flows, particularly in the Authorization Code Flow?
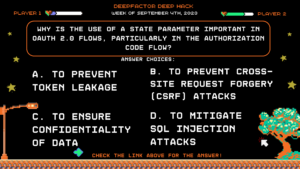
Question: Why is the use of a state parameter important in OAuth 2.0 flows, particularly in the Authorization Code Flow?
Answer Choices:
a) To prevent token leakage
b) To prevent Cross-Site Request Forgery (CSRF) attacks
c) To ensure confidentiality of data
d) To mitigate SQL injection attacks
Correct Answer: b) To prevent Cross-Site Request Forgery (CSRF) attacks
Explanation: The state parameter is used to maintain the state of the client’s request and protect against CSRF attacks. When the authorization server redirects the user back to the client after authentication, the client checks if the state parameter matches the one it sent in the initial request. This ensures that the authentication response originated from the client’s request and not from a malicious source.
Remediation: Always include a randomized state parameter when initiating the OAuth flow. Store the state on the server-side and validate it when the response is received. If the state doesn’t match, the client should not process the response. This prevents attackers from injecting unauthorized responses and stealing tokens. Understanding the importance of the state parameter helps developers implement secure OAuth flows, protecting against unauthorized access and attacks.
-
Deep Hack of the Week August 28th, 2023: What is prototype pollution?

Question: What is prototype pollution?
Answer Choices:
a) A Java vulnerability that enables an attacker to update an arbitrary database value by adding a parameter to the HTTP response
b) A JavaScript vulnerability that enables an attacker to add arbitrary properties to user-defined objects, which may then be inherited by global object prototypes
c) A JavaScript vulnerability that enables an attacker to add arbitrary properties to global object prototypes, which may then be inherited by user-defined objects
d) A TypeScript vulnerability that enables an attacker to add arbitrary properties to the proto property of user-defined objects
Correct Answer: d) A TypeScript vulnerability that enables an attacker to add arbitrary properties to the proto property of user-defined objects
Explanation:
Prototype pollution is a JavaScript vulnerability that enables an attacker to add arbitrary properties to global object prototypes, which may then be inherited by user-defined objects. This can be done by injecting malicious JavaScript code into the victim’s browser. The malicious JavaScript code can then add properties to the global object prototype, which will be inherited by all user-defined objects. This can be used to exploit other vulnerabilities in the application, such as cross-site scripting (XSS) vulnerabilities. -
Deep Hack of the Week August 21st, 2023: What is "dirty dancing" in sign-in OAuth-flows?

Question: What is “dirty dancing” in sign-in OAuth-flows?
Answer Choices:
a) An attack that exploits a vulnerability in the OAuth protocol to hijack a user’s account.
b) An attack that exploits a vulnerability in the OAuth protocol to steal a user’s authorization code.
c) An attack that exploits a vulnerability in the OAuth protocol to steal a user’s access token.
d) An attack that exploits a vulnerability in the OAuth protocol to redirect a user to a malicious website.
Correct Answer: a) An attack that exploits a vulnerability in the OAuth protocol to hijack a user’s account.
Explanation:
“Dirty dancing” is an attack that exploits a vulnerability in the OAuth protocol to hijack a user’s account. The attacker sends the victim a specially crafted link that contains a malicious state parameter. When the victim clicks on the link, they are redirected to the OAuth provider’s website. The OAuth provider then redirects the victim back to the website that sent the link, but the state parameter is now invalid. This causes the website to break the OAuth flow and the victim’s account is hijacked. -
Deep Hack of the Week August 14, 2023: What challenge is associated with the deployment of traditional container runtime security tools?
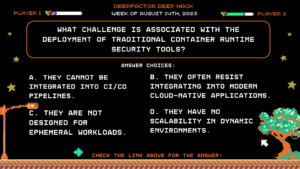
Question: What challenge is associated with the deployment of traditional container runtime security tools?
Answer Choices:
a) They cannot be integrated into CI/CD pipelines.
b) They often resist integrating into modern cloud-native applications.
c) They are not designed for ephemeral workloads.
d) They have no scalability in dynamic environments.
Correct Answer: b) They often resist integrating into modern cloud-native applications.
Explanation:
Traditional runtime security tools were designed before the advent of cloud-native architectures. They were mainly developed to work on monolithic applications that ran on physical servers or virtual machines. As cloud-native applications are designed to be scalable, resilient, and dynamic, the traditional tools often lack the capability to monitor and secure these new types of applications effectively. They might not easily integrate with the container orchestrations systems or be compatible with the rapidly changing nature of containers.
(If you haven’t yet, be sure to check out the new Container runtime security video to learn more!)
-
Deep Hack of the Week August 7, 2023: Which of these is a key advantage of using a defense-in-depth approach with container runtime security?

Question: Which of these is a key advantage of using a defense-in-depth approach with container runtime security?
Answer Choices:
a) Adding an additional layer of protection for cloud-native apps
b) Ensuring compatibility with non-containerized legacy systems
c) Reducing the number of containers within an application
d) Reducing the need for application-level encryption
Correct Answer: a) Adding an additional layer of protection for cloud-native apps
Explanation:
The term “defense-in-depth” refers to a multi-layered approach to security, where different kinds of security measures are implemented at different levels or stages to protect against potential threats. By incorporating container runtime security (CRS) into this approach, it adds an extra layer focused specifically on the runtime behavior of containers. This real-time analysis provides a critical layer of protection that complements other security measures, such as network security, secure coding practices, and access controls. When combined, these layers ensure that even if one defense mechanism fails or is bypassed, others are still in place to prevent or mitigate potential breaches.
(If you haven’t yet, be sure to check out the new Container runtime security video to learn more!)
-
Deep Hack of the Week July 31st, 2023: What is the best way to minimize false positives in the context of SCA?

Question: What is the best way to minimize false positives in the context of SCA?
Answer Choices:
a) By disregarding all vulnerabilities rated below a certain threshold
b) By offering rich context for each alert to reduce ambiguity
c) By running scans only during downtime to avoid false alerts due to active use
d) By focusing scans on proprietary rather than open source software components
Correct Answer: b) By offering rich context for each alert to reduce ambiguity
Explanation: False positives can create a significant drain on resources, as they might lead security professionals to investigate alerts that do not represent genuine security risks. This can also contribute to alert fatigue, where the volume of alerts (both genuine and false) is so high that important warnings might be overlooked. Options A, C, and D address general vulnerabilities, and not false positives directly.
(If you haven’t yet, be sure to check out the new SCA 2.0 whitepaper to learn more!)
-
Deep Hack of the Week July 24th, 2023: Which of the following is not included in the top 5 Evaluation Criteria for Developer Security Platforms?
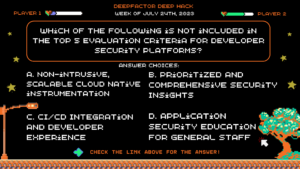
Question: Which of the following is not included in the top 5 Evaluation Criteria for Developer Security Platforms?
Answer Choices:
a) Non-intrusive, scalable cloud native instrumentation
b) Prioritized and comprehensive security insights
c) CI/CD integration and developer experience
d) Application security education for general staff
Correct Answer: d) Application security education for general staff
Explanation: The outlined elements critical to the success of introducing and driving DevSecOps adoption in organizations did not mention educating the general staff on all aspects of application security. Rather, the focus is on providing developers with timely, contextual, and actionable security insights. Each of the remaining answers are direct excerpts from the whitepaper.
(If you haven’t yet, be sure to check out the Top 5 Evaluation Criteria for Developer Security Platforms to learn more!)
-
Deep Hack of the Week July 17th, 2023: Deepfactor combines software composition analysis and container runtime security to reveal which of the following:
Question: Deepfactor combines software composition analysis and container runtime security to reveal which of the following:
Answer Choices:
a) Vulnerabilities in used packages that require updates
b) Unnecessary application components that contribute to the CVE debt
c) Unused packages that can potentially be removed
d) All of the above
Correct Answer: d) All of the above
Explanation: Deepfactor correlates SCA scan results with runtime analysis to identify vulnerabilities in both used and unused packages. When a vulnerability exists in a used package, it is assigned to a developer to be fixed or updated based on the criticality of the issue. If there is a vulnerability in a package that is not used, the engineering team can consider removing the package in the next build or switch to a different base image to eliminate the known vulnerability.
(If you haven’t yet, be sure to check out the Moogsoft Case Study to learn more!)
-
Deep Hack of the Week July 10th, 2023: Which of the following does Deepfactor's Container Runtime Security work to expose?

Question: Which of the following does Deepfactor’s Container Runtime Security work to expose?
Answer Choices:
a) Privilege escalation
b) Prohibited network communications
c) Sensitive information
d) All of these answers
Correct Answer: d) All of these answers
Explanation: Deepfactor Container Runtime Security monitors applications in production environments to detect runtime security risks in filesystem, network, process, and memory behavior including exposing sensitive information, privilege escalation, and prohibited network communications. Runtime security in production environments helps demonstrate compliance (SOC 2, etc.) and uncovers indicators of compromise by pinpointing suspicious file, network, and memory behaviors.
(Make sure to tune in to our upcoming webinar on July 12th! )
-
Deep Hack of the Week June 26th, 2023: Which of the following software security vulnerabilities is NOT classified as an injection attack?
Question: Which of the following software security vulnerabilities is NOT classified as an injection attack?
Answer Choices:
a) SQL Injection
b) Cross-site Scripting (XSS)
c) Denial-of-service attack (DOS)
d) Cross-Site Request Forgery (CSRF)
Correct Answer: c) Denial-of-service attack (DOS)
Explanation: Denial of Service (DOS) attacks are not considered injection attacks because they operate by overwhelming a target system or resource, rendering it unavailable to legitimate users. Injection attacks, on the other hand, involve exploiting vulnerabilities in software by inserting malicious code or commands into input fields or data streams to manipulate the system’s behavior.
(If you haven’t seen it yet, check out the 12-minute Deepfactor demo video.)
-
Deep Hack of the Week June 19th, 2023: Which of the following are benefits of container runtime security?

Question: Which of the Following are Benefits of Container Runtime Security?
Answer Choices:
a) Isolation of containers to prevent cross-container attacks
b) Continuous monitoring of container activity for malicious behavior
c) Secure container image scanning for vulnerabilities in Dev & Test
d) All of these choices.
Correct Answer: d) All of these choices.
Explanation: Container runtime security is crucial for protecting containerized applications and their underlying infrastructure from various threats, such as unauthorized access, malware, data breaches, and configuration vulnerabilities. By implementing comprehensive security measures, organizations can ensure the integrity, availability, and confidentiality of their containerized environments.
(Make sure to tune in to our upcoming webinar on July 12th! )
-
Deep Hack of the Week June 12th, 2023: Which of the Following Strategies can Help Mitigate Dependency Confusion Vulnerabilities?

Question: Which of the Following Strategies can Help Mitigate Dependency Confusion Vulnerabilities?
Answer Choices:
a) Using private package repositories or registries.
b) Locking down permissions on internal package repositories.
c) Using multi-factor authentication for package uploads.
d) All of these choices.
Correct Answer: d) All of these choices.
Explanation: To mitigate Dependency Confusion vulnerabilities, developers can use private package repositories or registries, lock down permissions on internal package repositories, and use multi-factor authentication for package uploads. These strategies can help ensure that only authorized packages are used in an application, reducing the risk of malicious packages being introduced.
(If you haven’t seen it yet, check out the 12-minute Deepfactor demo video.)
-
Deep Hack of the Week June 5th, 2023: What is a Dependency Confusion Vulnerability?

Question: What is a Dependency Confusion Vulnerability?
Answer Choices:
a) A vulnerability that occurs when an attacker gains access to a system through a misconfigured or unsecured dependency.
b) A vulnerability that allows an attacker to modify or inject malicious code into an application’s dependencies.
c) A vulnerability that occurs when an application uses a public package with the same name as an internal package.
Correct Answer: c) A vulnerability that occurs when an application uses a public package with the same name as an internal package.
Explanation: Dependency Confusion vulnerabilities occur when an application uses a public package repository, such as npm or PyPI, and also has internal packages with the same name. If an attacker uploads a malicious package with the same name as an internal package, the application may unintentionally download and use the malicious package, leading to potential security vulnerabilities.
(If you haven’t seen it yet, check out the 12-minute Deepfactor demo video.)
-
Deep Hack of the Week May 29th, 2023: Which HTTP header is commonly used to trigger the H2C Smuggling vulnerability?
Question: Which HTTP header is commonly used to trigger the H2C Smuggling vulnerability?
Answer Choices:
a) Content-Length
b) Transfer-Encoding
c) Upgrade
d) Connection
Correct Answer: b) Transfer-Encoding
Explanation: The H2C Smuggling vulnerability is often triggered by manipulating the Transfer-Encoding header, which is used to specify the encoding used for the message body. By crafting an HTTP request with multiple Transfer-Encoding headers, or by using other techniques to manipulate the header, an attacker can trigger the vulnerability and bypass security controls.
(If you haven’t seen it yet, check out the 12-minute Deepfactor demo video.)
-
Deep Hack of the Week May 15, 2023: What is the H2C Smuggling vulnerability?
Question: What is the H2C Smuggling vulnerability?
Answer Choices:
a) A vulnerability that allows attackers to hijack an H2C connection and steal sensitive information.
b) A vulnerability that allows attackers to bypass web application firewalls by smuggling HTTP requests over H2C.
c) A vulnerability that allows attackers to perform server-side request forgery (SSRF) attacks over H2C connections.
Correct Answer: b) A vulnerability that allows attackers to bypass web application firewalls by smuggling HTTP requests over H2C.
Explanation: The H2C Smuggling vulnerability occurs when an attacker sends HTTP requests over an H2C (HTTP/2 over cleartext TCP) connection in a way that bypasses security controls such as web application firewalls. By exploiting differences in the way H2C and HTTP/1.x handle HTTP pipelining and chunked encoding, an attacker can craft a request that appears valid to the web application but is interpreted differently by the H2C connection and the firewall.
(If you haven’t seen it yet, check out the 12-minute Deepfactor demo video.)
-
Deep Hack of the Week April 24, 2023: What is the Psychic Signature vulnerability in Java?

Question: What is the Psychic Signature vulnerability in Java?
Answer Choices:
a) A vulnerability that allows an attacker to bypass security restrictions in the Java runtime environment.
b) A vulnerability that can occur when a method is invoked with an object of a different type than expected, causing an unsafe cast.
c) A vulnerability that allows an attacker to execute arbitrary code on a system through a Java applet.
Correct Answer: b) A vulnerability that can occur when a method is invoked with an object of a different type than expected, causing an unsafe cast.
Explanation: When a method takes a parameter of a specific type in Java, if the method is invoked with an object of a different type, the Java runtime may perform an unsafe cast to automatically convert the object to the expected type. This can lead to unexpected behavior and potential vulnerabilities. (If you haven’t seen it yet, check put the 12-minute Deepfactor demo video.)
-
Deep Hack of the Week April 17, 2023: What is EPSS?

Question: What is EPSS?
Answer Choices:
a) An open, data-driven framework for estimating the likelihood that a software vulnerability will be exploited in the wild.
b) A scoring system that outputs a probability of the estimated likelihood of exploitation from 0 to 1 or 0% to 100%.
c) A community-driven effort to combine descriptive information about vulnerabilities (CVEs) with evidence of actual exploitation in-the-wild.
d) All of the above.
Correct Answer: d) All of the above.
Explanation: EPSS is an open, data-driven framework for estimating the likelihood that a software vulnerability will be exploited in the wild. It is a community-driven effort to combine descriptive information about vulnerabilities (CVEs) with evidence of actual exploitation in the wild. The EPSS model produces a probability score between 0 and 1 or 0% and 100%. The higher the score, the greater the probability that a vulnerability will be exploited. (If you haven’t seen it yet, check put the 12-minute Deepfactor demo video.)
-
Deep Hack of the Week April 10, 2023: Which of the following is a potential consequence of the Psychic Signature vulnerability in Java?
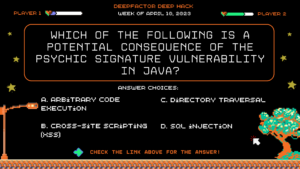
Question: Which of the following is a potential consequence of the Psychic Signature vulnerability in Java?
Answer Choices:
a) Arbitrary code execution
b) Cross-site scripting (XSS)
c) Directory traversal
d) SQL injection
Correct Answer: a) Arbitrary code execution
Explanation: Because the Psychic Signature vulnerability can cause an unsafe cast, an attacker may be able to provide an object of their own choosing that can be cast to a malicious class, potentially allowing for arbitrary code execution.
-
Deep Hack of the Week Mar 27, 2023: What is In a software bill of materials (SBOM) list?
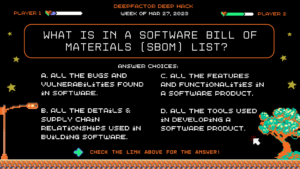
Question: What is In a software bill of materials (SBOM) list?
Answer Choices:
a) All the bugs and vulnerabilities found in software.
b) All the details & supply chain relationships used in building software.
c) All the features and functionalities in a software product.
d) All the tools used in developing a software product.
Correct Answer: b) All the details & supply chain relationships used in building software.
Explanation: According to the U.S. National Institute of Standards and Technology (NIST), an SBOM is “a formal record containing the details and supply chain relationships of various components used in building software. Software developers and vendors often create products by assembling existing open source and commercial software components. The SBOM enumerates these components in a product.” Check out Deepfactor resources on SBOM, including the whitepaper SBOM Security: Top 5 Reasons to Build SBOMs Into Your Pipeline and the webinar with Cisco and VMware, Integrating SBOMs Into Your SDLC by the Biden Executive Order June Deadline.
-
Deep Hack of the Week Mar 22, 2023: When is the White House Executive Order deadline for software supply chain requirements?
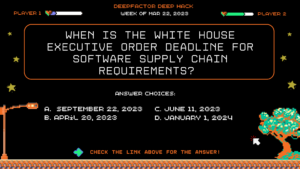
Question: When is the White House Executive Order deadline for software supply chain requirements?
Answer Choices:
a) September 22, 2023
b) April 20, 2023
c) June 11, 2023
d) January 1, 2024
Correct Answer: June 11, 2023
Explanation: Executive Order (EO) 14028, Improving the Nation’s Cybersecurity (May 12, 2021), focuses on the security and integrity of the software supply chain and emphasizes the importance of secure software development environments. This memorandum sets a schedule of deliverables for federal agencies to follow. Within 90 days from the distribution of M-22-18, they must identify and inventory all software subject to the requirements of the memo and make a separate inventory of “critical software.” And within 270 days (by June 11, 2023) of the distribution of the memo, agencies need to have collected attestation letters (i.e. evidence) for any critical software they have identified.
-
Deep Hack of the Week Mar 15, 2023: What type of vulnerability is present in the following Java code snippet which is supposed to return their own profile information to a user?
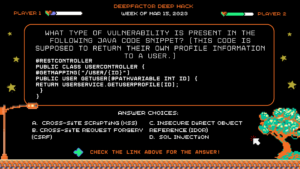
Question: What type of vulnerability is present in the following Java code snippet? (This is supposed to return their own profile information to a user.)
@RestController
public class UserController {
@GetMapping(“/user/{id}”)
public User getUser(@PathVariable int id) {
return userService.getUserProfile(id);
}
}
Answer Choices:
a) Cross-Site Scripting (XSS)
b) Cross-Site Request Forgery (CSRF)
c) Insecure Direct Object Reference (IDOR)
d) SQL Injection
Correct Answer:
c) Insecure Direct Object Reference (IDOR)
Explanation: The code snippet is a RESTful web service that retrieves user information by calling userService.getUser(id) with the id parameter from the URL. If proper access controls are not implemented, an attacker could manipulate the id parameter in the URL to access information for users that they should not have access to, leading to an IDOR vulnerability, also called Broken Object Level Authorization (BOLA). This vulnerability can be mitigated by implementing proper access controls and validating user input.
Learn how Deepfactor developer security prioritizes your alerts here!
-
Deep Hack of the Week Mar 7, 2023: What is "SBOM"?

Question: What is “SBOM”?
Answer Choices:
a. System Build Object Model
b. Secure Bounds of Memory
c. Software Bill of Material
d. Security-Based Override Mitigation
Correct Answer:
c. Software Bill of Materials
Explanation: A Software Bill of Materials (SBOM) is a complete, formally structured list of components, libraries, and modules that are required to build (i.e. compile and link) a given piece of software and the supply chain relationships between them. These components can be open source or proprietary, free or paid, and widely available or restricted access.
Watch and learn more about Deepfactor’s Software Bill of Materials!
Read the whitepaper “SBOM Security: Top 5 Reasons to Build SBOMs Into Your Pipeline”
-
Deep Hack of the Week Mar 1, 2023: What is a type confusion vulnerability?
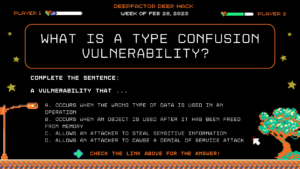
Question: What is a type confusion vulnerability?
Complete the sentence: “A vulnerability that…”
a. Occurs when the wrong type of data is used in an operation
b. Occurs when an object is used after it has been freed from memory
c. Allows an attacker to steal sensitive information
d. Allows an attacker to cause a denial of service attack
Correct Answer: B) A vulnerability that occurs when an object is used after it has been freed from memory.
Explanation: A use-after-free vulnerability is a type of security vulnerability that occurs when an object is used after it has been freed from memory. This can result in unexpected behavior, such as memory corruption or arbitrary code execution. Runtime security tools can help detect use-after-free vulnerabilities by monitoring the memory management of an application and checking for any issues with object deallocation and reuse.
Learn how Deepfactor developer security prioritizes your alerts here!
-
Deep Hack of the Week Feb 22, 2023: What is a common method used by attackers to penetrate software supply chains?

Question: What is a common method used by attackers to penetrate software supply chains?
Answer Choices:
a. Social engineering
b. Brute force attacks
c. Drive-by downloads
d. Watering hole attacks
Correct Answer: Watering hole attacks
Explanation: A watering hole attack is a type of supply chain attack in which an adversary targets a specific website or group of websites that is frequently visited by a target group, such as employees of a particular company. By compromising these sites, the attacker can infect systems with malware or steal sensitive information when the target group visits the site. This type of attack is often used to penetrate software supply chains and target specific organizations.
Learn how Deepfactor developer security prioritizes your alerts here!
-
Deep Hack of the Week Feb 15, 2023: Which of the following vulnerabilities is demonstrated in this code snippet?
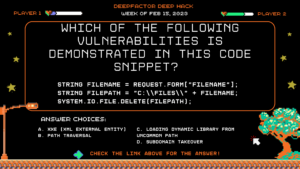
Question: Which of the following vulnerabilities is demonstrated in this code snippet?
string fileName = Request.Form[“fileName”];
string filePath = “C:\\files\\” + fileName;
System.IO.File.Delete(filePath);
Answer Choices:
a. XXE (XML External Entity)
b. Path Traversal
c. Loading dynamic library from uncommon path
d. Subdomain takeover
Correct Answer: Path Traversal
Explanation: In this program the first line indicates that the fileName variable is being read from user input that comes from a web form. This is directly appended to a filePath without any input validation. This means, special characters like ../../ could be used to allow the file to be written to a directory outside the intended directory, or to overwrite system files.
Learn how Deepfactor developer security prioritizes your alerts here!
-
Deep Hack of the Week Feb 6, 2023: Which of the following is NOT a best practice for securing the supply chain?

Question: Which of the following is NOT a best practice for securing the supply chain?
Answer: Using only open source software components
Explanation: All open source software components are not secure. There have been several instances recently where an attacker took over as a maintainer of a well-known open source library and updated it with malicious code. Watch and learn how Deepfactor breaks down your runtime alerts in this example highlighting a suspicious outbound connection.
-
Deep Hack of the Week Jan 30, 2023: Which of the following is NOT a common vulnerability in backend software?

Question: Which of the following is NOT a common vulnerability in backend software?
Answer: Cross-Site Scripting
Explanation: Cross-Site Scripting is a common frontend exploit. To learn more about runtime security alerts watch this quick clip!
-
Deep Hack of the Week Jan 23, 2023: True or False—If you use open source libraries with known CVE you are 100% vulnerable to attacks.
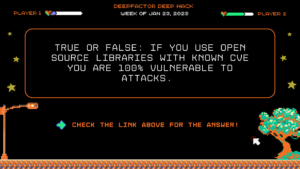
Question: True or False—If you use open source libraries with known CVE you are 100% vulnerable to attacks.
Answer: False
If you use an open source library with known CVE, there is a likelihood that you are vulnerable to attacks, but it isn’t 100% certain. It is possible that you are not calling the vulnerable function or method call in your code and therefore your software is not vulnerable to attack. Traditional security tools like SAST or DAST do not provide runtime visibility into program behavior to give you full context about the exploitability of the vulnerability within your application. Modern tools like Deepfactor identify runtime risks, finding vulnerabilities in dev and test that are missed by static scanning. Watch this quick clip!
-
Deep Hack of the Week Jan 16, 2023: What percentage of a software code repository is usually third-party libraries?
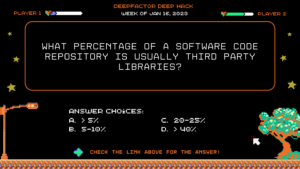
Question: What percentage of a software code repository is usually third-party libraries?
Answer: Greater than 40%
Most developers do not realize the number of direct and indirect third-party dependencies that get pulled into their code repositories when they import a small number of dependencies. In fact node.js, one of the most notorious frameworks for having transitive dependenices, has libraries that pull more than 1000 of them. See how Deepfactor Developer Security can help. Watch this quick clip!
-
Deep Hack of the Week Jan 9, 2023: Find the security flaw in the following code snippet.
Question: Find the security flaw in the following code snippet:
from flask import Flask import requests app = Flask(__name__) @app.route("/", methods=['GET','POST']) def home(): if request.method == 'POST': URL = request.form.get('url') r = requests.get(url = URL, headers=headers) body = r.text header = r.headersAnswer: SSRF
This program starts with an import of Flask, which is an indicator that this code snippet is using Python Flask framework and is backend code. If you observe deeply, you will notice that the URL parameter is coming from the client side (HTTP form) and is being directly used in requests.get, which allows an attacker to induce a connection to an internal resource.
Background / Context: Server-side request forgery (also known as SSRF) is a web security vulnerability that allows an attacker to induce the server-side application to make requests to an unintended location. In a typical SSRF attack, the attacker might cause the server to make a connection to internal-only services within the organization’s infrastructure. In other cases, they may be able to force the server to connect to arbitrary external systems, potentially leaking sensitive data such as authorization credentials. See how Deepfactor Developer Security can help. Watch this quick clip!
-
Deep Hack of the Week Jan 2, 2023: How can an attacker steal your credentials?
Question: How can an attacker steal credentials directly from your own application without having a victim browse to a phishing site?
Answer: If your application has a Cross Site Scripting (XSS) flaw, it is possible for the attacker to run javascript within your application’s webpage. Using this capability, an attacker can create a legitimate-looking login form, within your own web application. See how Deepfactor Developer Security can help. Watch this quick clip!