Deepfactor can scan software artifacts such as container images and source code to generate software bill of materials (SBOM) and find SCA vulnerabilities. In order to allow scanning at different stages of the SDLC, Deepfactor provides the following different ways of scanning artifacts
- Deepfactor CLI (dfctl): Developers can scan their code/container images in the terminal using dfctl. Refer to the following article to understand how to scan artifacts using Deepfactor CLI
Scanning your artifacts with dfctl - Deepfactor CLI container image: Deepfactor also packages the CLI, dfctl in a container image which can be used in CI/CD pipelines to run scans against your images or file sytems. Refer to the following article to understand how you can use this container image in your CI/CD pipelines
Integrate Deepfactor scanner in your CI/CD pipelines - Deepfactor K8s scan pod: Deepfactor can deploy one or more scan pods in your K8s cluster which will automatically scan container images used by pods launched in your K8s cluster.
In order for Deepfactor to access and scan container images from private registries, you will need to specify registry credentials. Refer to the following article to understand how to pass registry credentials to Deepfactor scanner.
Scanning images from private registries using Deepfactor
Deepfactor Scanner data sources #
Deepfactor regularly pulls vulnerability feeds from the following data sources.
Data sources for OS package vulnerabilities #
| OS | Source |
|---|---|
| Arch Linux | Vulnerable Issues |
| Alpine Linux | secdb |
| Wolfi Linux | secdb |
| Chainguard | secdb |
| Amazon Linux | Amazon Linux Security Center |
| Debian | Security Bug Tracker |
| OVAL | |
| Ubuntu | Ubuntu CVE Tracker |
| RHEL/CentOS | OVAL |
| Security Data | |
| AlmaLinux | AlmaLinux Product Errata |
| Rocky Linux | Rocky Linux UpdateInfo |
| Oracle Linux | OVAL |
| CBL-Mariner | OVAL |
| OpenSUSE/SLES | CVRF |
| Photon OS | Photon Security Advisory |
Data sources for Language specific dependency vulnerabilities #
| Language | Source |
|---|---|
|
PHP |
|
|
|
|
|
Python |
|
|
|
|
|
Ruby |
|
|
|
|
|
Node.js |
|
|
|
|
|
Java |
|
|
|
|
|
Go |
|
|
|
|
|
Rust |
|
|
.NET |
|
|
C/C++ |
|
|
Dart |
|
|
Elixir |
Deepfactor Scanner results #
Deepfactor scanner supports the following output formats
- CycloneDX compliant SBOM
- SPDX compliant SBOM as key value and/or json
- Deepfactor json format
- Table
You can view the results in above formats in the following ways
- On the terminal output if you are using dfctl
- As a file stored on disk where the scan is performed
- As a CI/CD pipeline output artifact
- On the Deepfactor portal UI
The Deepfactor portal UI shows the results of each scan performed and also the history of scans for older versions of the artifacts. This allows you to compare the results across versions of your artifacts.
Offline scans #
Deepfactor scan errors
Note: As mentioned above, Deepfactor automatically detects certain types of errors and restarts the scans in offline mode. This can result in higher scan times and some scans may timeout. In such cases, please increase the scan timeout using the -u option as described in the following article
Scanning your artifacts with dfctl
#
Base image layer detection #
Deepfactor can automatically detect layers that belong to the base image without the need for the user to pass the Dockerfile to the dfctl scan command. Deepfactor uses the following logic to detect base image layers
- Get image history to get the full list of layers
- Traverse the layers to identify the occurrence of a CMD/ENTRYPOINT instruction after the first encountered non empty layer.
- Mark all layers post the encountered CMD/ENTRYPOINT (inclusive) instruction as base image layers
Example:
docker history tomcat
The above command will provide the following output
e46faef801b7 5 days ago /bin/sh -c #(nop) CMD ["catalina.sh" "run"] 0B <missing> 5 days ago /bin/sh -c #(nop) EXPOSE 8080 0B <missing> 5 days ago /bin/sh -c set -eux; nativeLines="$(catalin… 0B <missing> 5 days ago /bin/sh -c set -eux; savedAptMark="$(apt-m… 21.8MB <missing> 5 days ago /bin/sh -c #(nop) ENV TOMCAT_SHA512=ad754aa… 0B <missing> 5 days ago /bin/sh -c #(nop) ENV TOMCAT_VERSION=10.1.11 0B <missing> 5 days ago /bin/sh -c #(nop) ENV TOMCAT_MAJOR=10 0B <missing> 5 days ago /bin/sh -c #(nop) ENV GPG_KEYS=5C3C5F3E314C… 0B <missing> 5 days ago /bin/sh -c #(nop) ENV LD_LIBRARY_PATH=/usr/… 0B <missing> 5 days ago /bin/sh -c #(nop) ENV TOMCAT_NATIVE_LIBDIR=… 0B <missing> 5 days ago /bin/sh -c #(nop) WORKDIR /usr/local/tomcat 0B <missing> 5 days ago /bin/sh -c mkdir -p "$CATALINA_HOME" 0B <missing> 5 days ago /bin/sh -c #(nop) ENV PATH=/usr/local/tomca… 0B <missing> 5 days ago /bin/sh -c #(nop) ENV CATALINA_HOME=/usr/lo… 0B <missing> 5 days ago /bin/sh -c #(nop) CMD ["jshell"] 0B <missing> 5 days ago /bin/sh -c #(nop) ENTRYPOINT ["/entrypoint.… 0B <missing> 5 days ago /bin/sh -c #(nop) COPY file:0673fe0a4a716089… 1.08kB <missing> 5 days ago /bin/sh -c echo Verifying install ... &&… 0B <missing> 5 days ago /bin/sh -c set -eux; ARCH="$(dpkg --prin… 279MB <missing> 5 days ago /bin/sh -c #(nop) ENV JAVA_VERSION=jdk-17.0… 0B <missing> 11 days ago /bin/sh -c apt-get update && DEBIAN_FRON… 50MB <missing> 5 weeks ago /bin/sh -c #(nop) ENV LANG=en_US.UTF-8 LANG… 0B <missing> 5 weeks ago /bin/sh -c #(nop) ENV PATH=/opt/java/openjd… 0B <missing> 5 weeks ago /bin/sh -c #(nop) ENV JAVA_HOME=/opt/java/o… 0B <missing> 6 weeks ago /bin/sh -c #(nop) CMD ["/bin/bash"] 0B <missing> 6 weeks ago /bin/sh -c #(nop) ADD file:140fb5108b4a2861b… 77.8MB <missing> 6 weeks ago /bin/sh -c #(nop) LABEL org.opencontainers.… 0B <missing> 6 weeks ago /bin/sh -c #(nop) LABEL org.opencontainers.… 0B <missing> 6 weeks ago /bin/sh -c #(nop) ARG LAUNCHPAD_BUILD_ARCH 0B
In the above list,
- Row 4 is the first non empty layer
- Row 15 is the first encountered CMD/ENTRYPOINT instruction. Hence, rows 15 to 29 are marked as base image layers
The following approach assumes that
- Each base image’s Dockerfile will have at least a CMD or Entrypoint instruction. This is true for most commonly used base images.
- The container image is built on top of one or more base images (using FROM instruction) Dockerfile reference , Multi-stage builds
#
Artifact Releases #
Deepfactor allows you to tag scans to a particular release of your software artifact. Software teams generally generate several builds per day in their CI/CD pipeline. Once integrated in the CI/CD pipeline or K8s cluster, Deepfactor will scan every build. However, it becomes a tedious task to go through the scan results of all of these builds and teams generally care about the latest state of their release build and want to answer the following questions:
- What is the security posture of the artifact build that is currently running in production?
- What is the security posture of the latest build of the upcoming release which is under development?
- What is the trend of vulnerabilities within a release? Are my developers reducing the vulnerability count on a per release basis?
- What is the trend of vulnerabilities across releases? Over a period of time, has the security posture for an artifact improved or has it gotten worse?
In order to help teams answer the above questions, Deepfactor has introduced the capability for users to tag a certain scan as belonging to a certain release. Once the user specifies the release for scans, Deepfactor shows the trend of vulnerabilities across builds within a single release and across the releases over a period of time. You can read more about artifact releases here.
Deepfactor’s correlation capabilities #
Deepfactor can scan your artifacts (container images / file system directories) to generate SBOM and find SCA vulnerabilities. Deepfactor can also observe running containers / non-containerized applications to detect runtime risks. The unique capability Deepfactor provides is that it can correlate the results of the scan and runtime observation so you get
- An unified view of your application’s security posture
- Additional information so you can priortize which vulnerabilities to fix earlier than others.
You can read more about Deepfactor’s correlation capabilities here.
Deepfactor artifacts UI #
The following section describes the UI pages shown on the portal for artifact results.
Artifacts Dashboard #
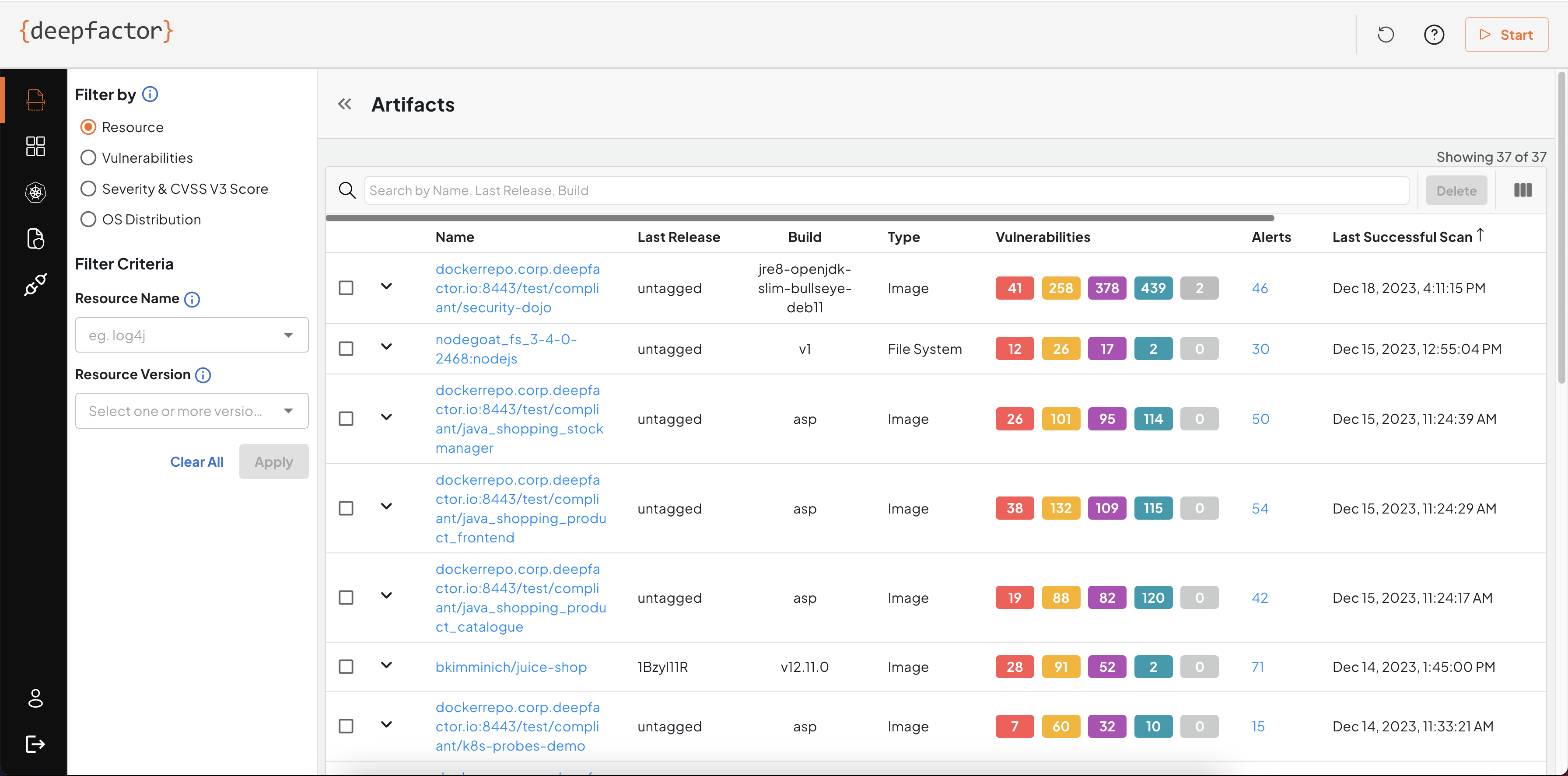
You can see the artifacts dashboard by navigating to Artifacts from the left sidebar.
Artifacts page shows the list of artifacts (images and filesystems) scanned along with results of the last successful scan.
Artifact Name
Deepfactor uses a unique name for each artifact and stores the results of all subsequent scans of the same or different versions of the artifact under that artifact name.
In the case of container images, the artifact name is the image path without the tag.
Example:
For the image, deepfactor.repo:8442/myservice:version1
Artifact name: deepfactor.repo:8442/myservice
Version: version1
Subsequently, if you scan deepfactor.repo:8442/myservice:version2, version2 will be considered another version of the same artifact, deepfactor.repo:8442/myservice:version1
In the case of file system scans, you will need to provide the following details:
- application name
- component name
- component version
Deepfactor use the concatenation of application name and component name as artifact name and the component version as the version of the artifact.
Example:
If you used the following command to scan
dfctl scan -s fs -a “myapp” -c “mycomp” -V “1.0” mydir/service
Artifact name: myapp:mycomp
Artifact version: 1.0
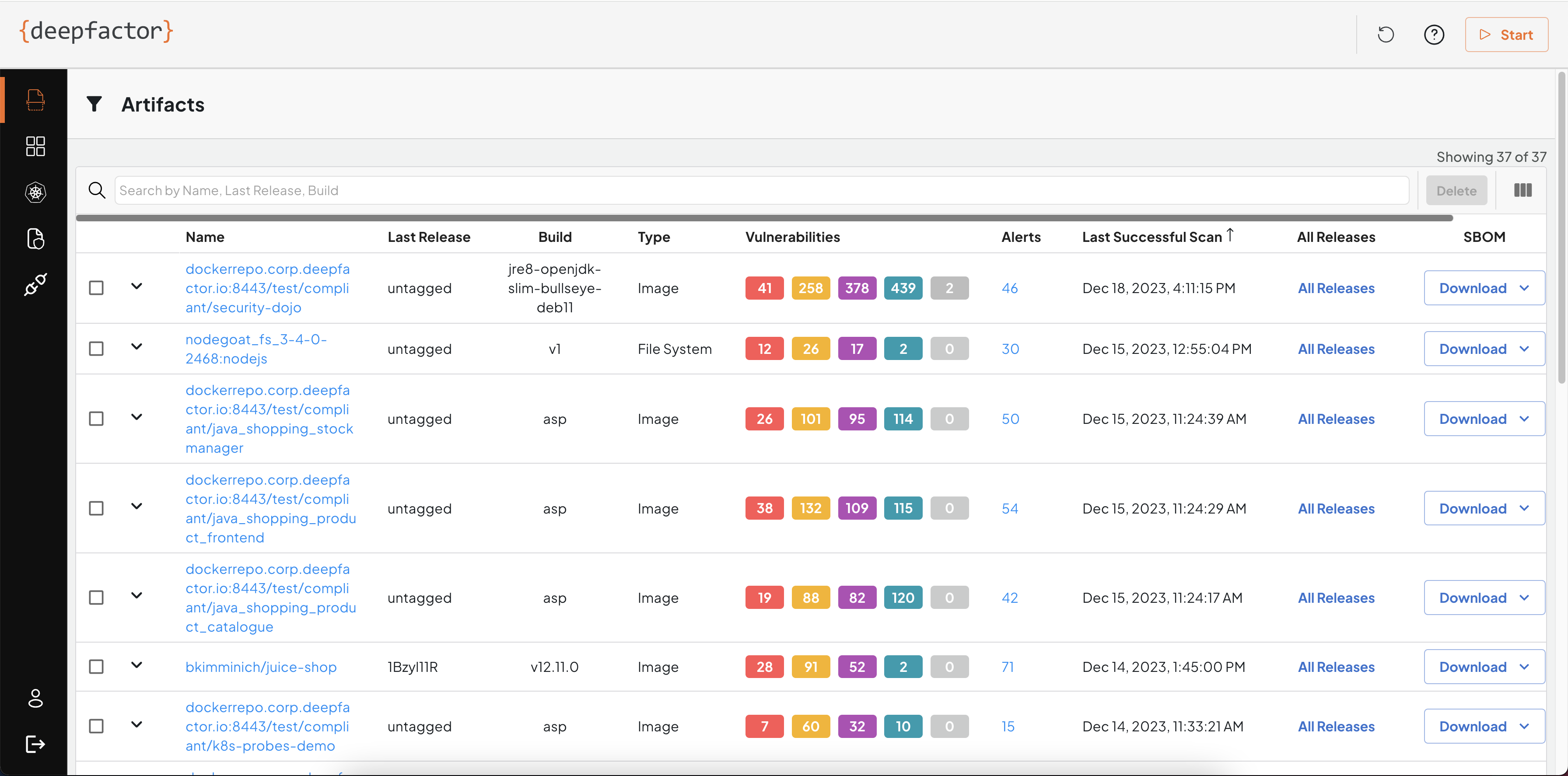
If you would like to see the results of older releases of your artifacts, you can click on the All Releases button
Artifact Scan Results #
The results of the scan are shown under multiple tabs on the UI. The following section describes the information shown in the different tabs
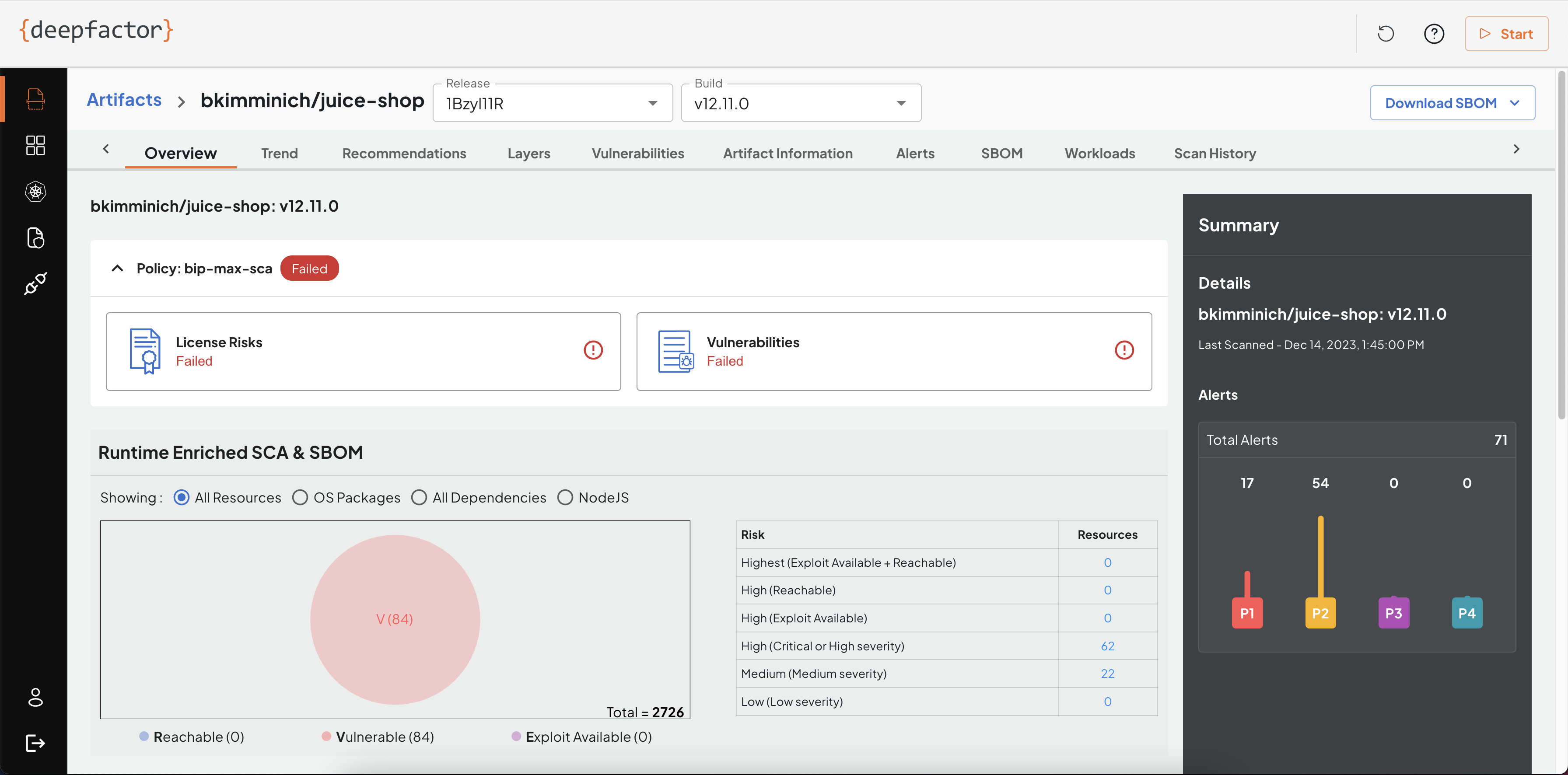
Overview
The overview tab gives a summary of the scan results such as policy violations, general information about the artifact and vulnerabilities.
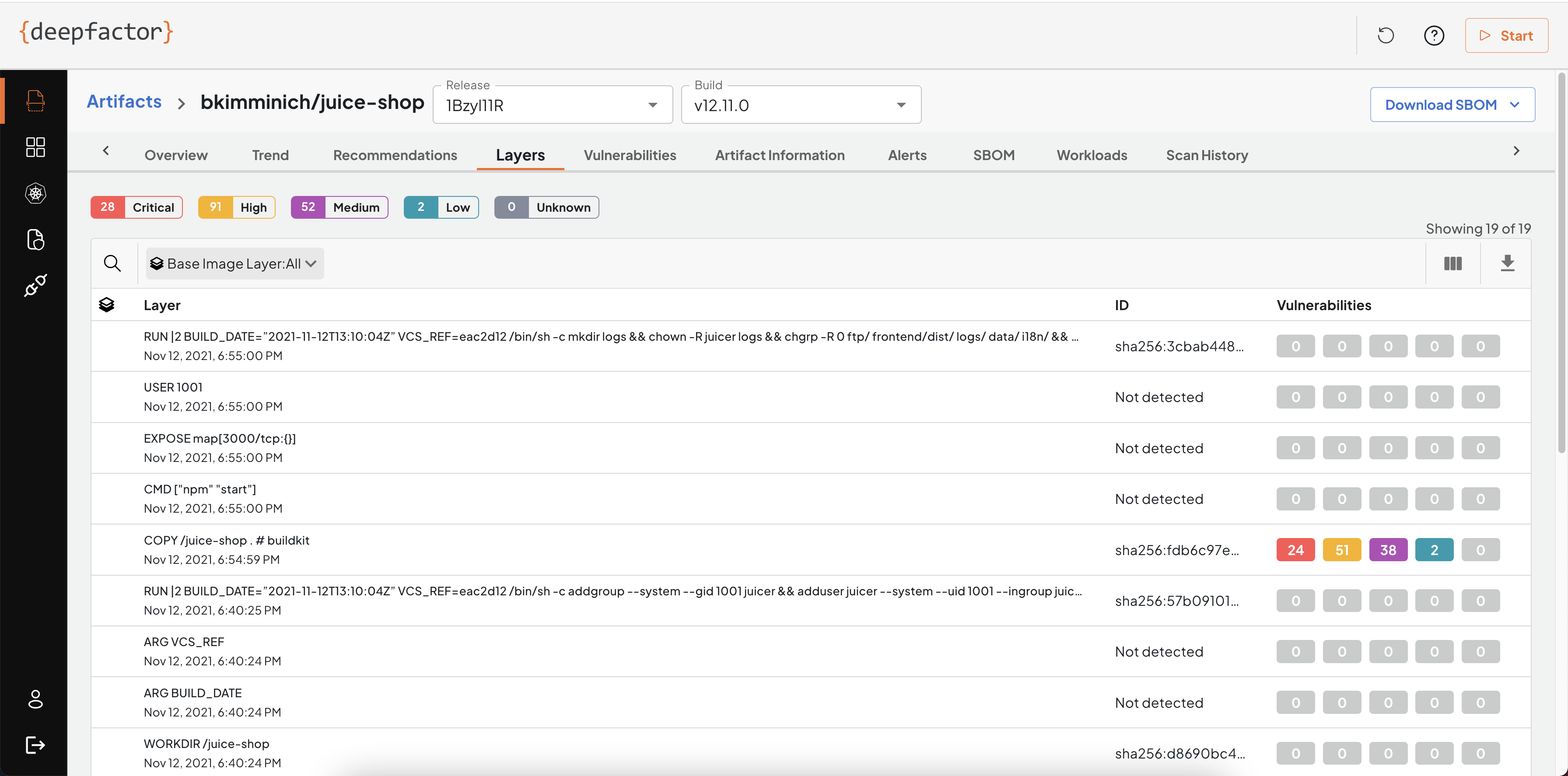
Layers
Deepfactor detects the different layers found in your container images and also ties the vulnerabilities to the layer it is found in. This will help your developers identify if the vulnerability is present in the base image or due to a command in the Dockerfile used to generate the image.
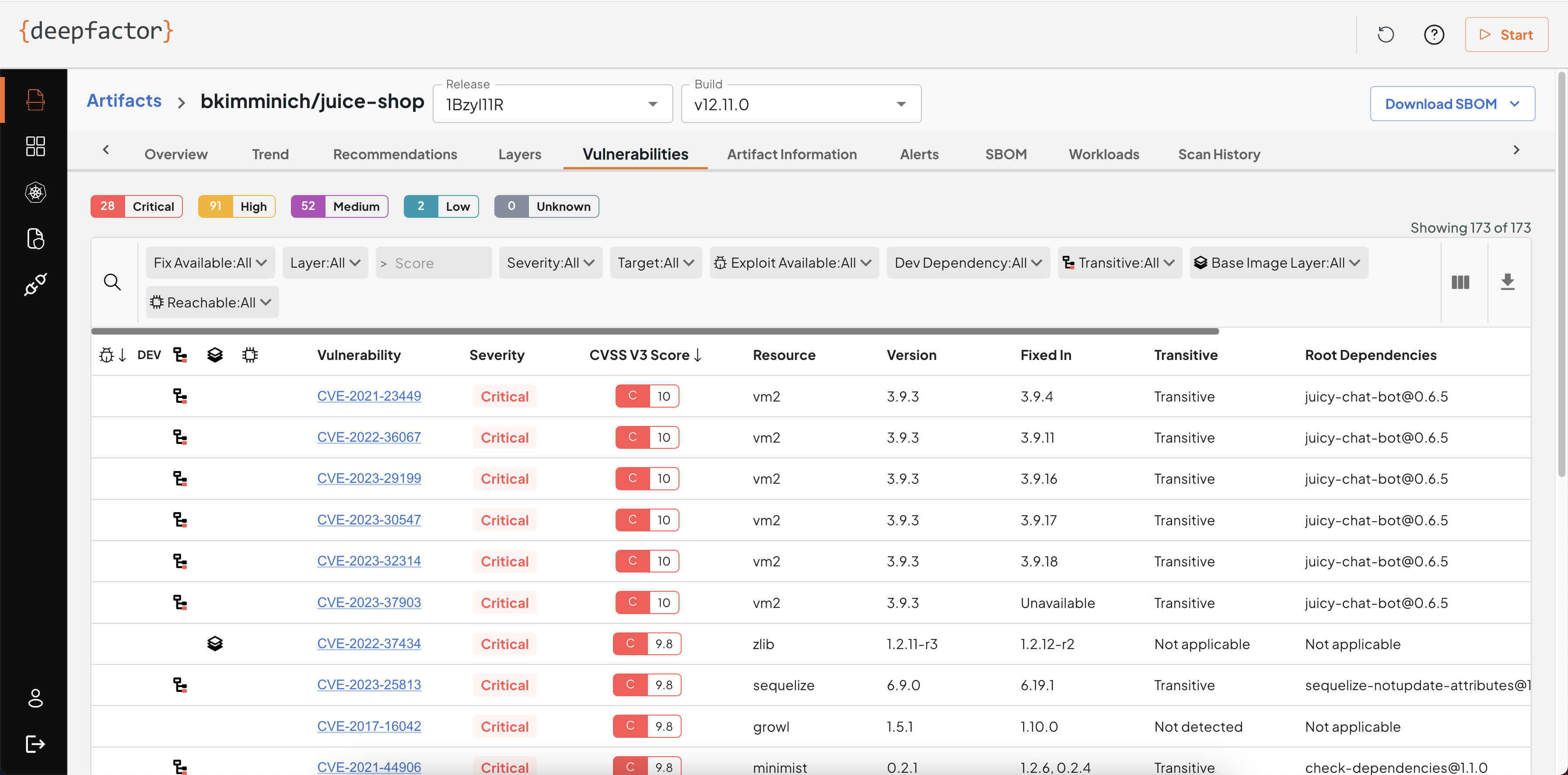
Vulnerabilities
This tab lists the full list of vulnerabilities found in the container image. Each vulnerability is tied to a resource, resource version and target. If your container image has multiple applications such as a java application, a go binary, a python project etc, Deepfactor will detect them and also tag each vulnerability to the application target within the container.
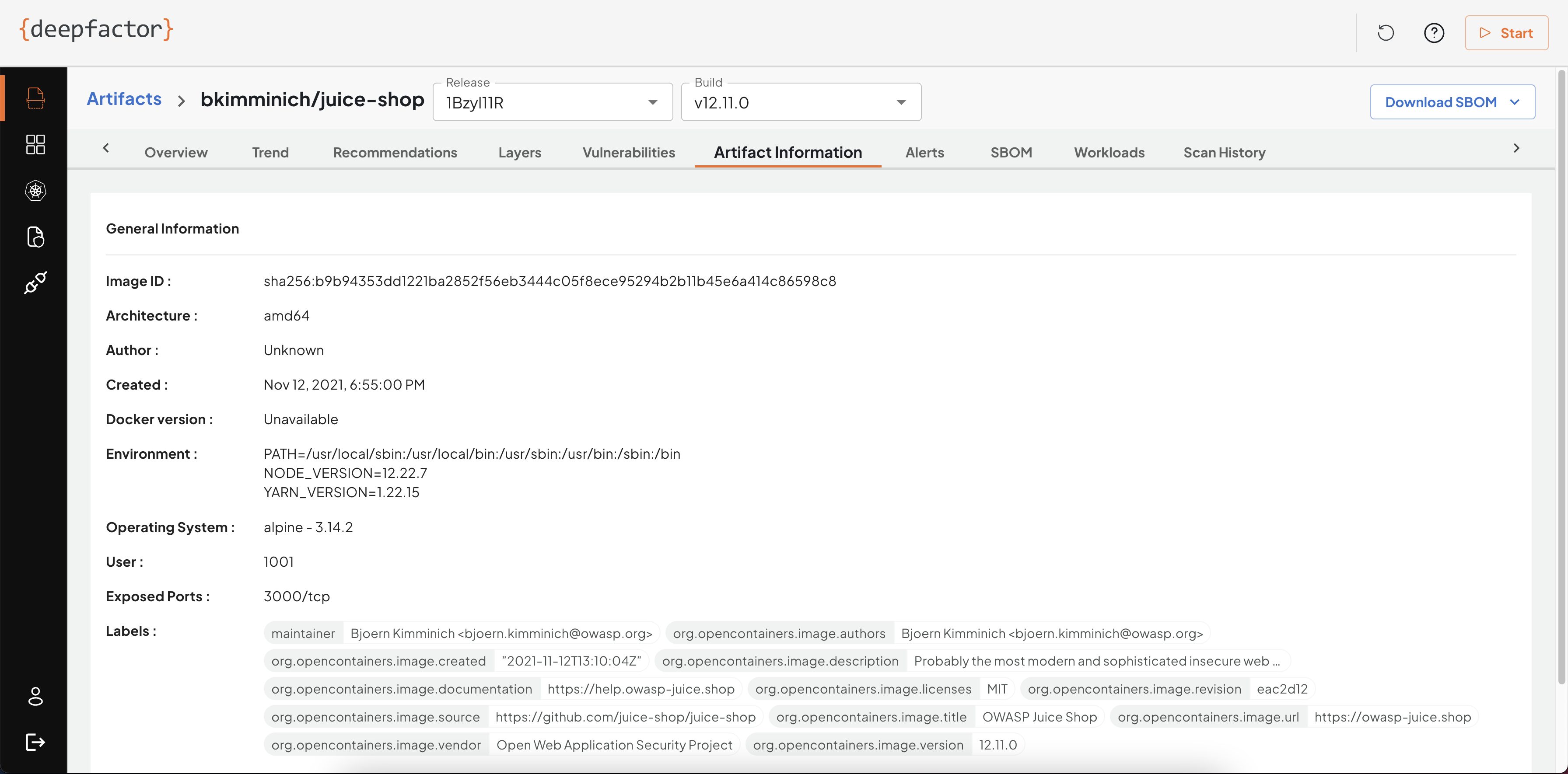
Artifact Information
This tab provides basic information about the scanned artifact including environment variables. Sometimes sensitive information is passed as environment variables which is a bad security practice. Please ensure you remove any sensitive information from environment variables.
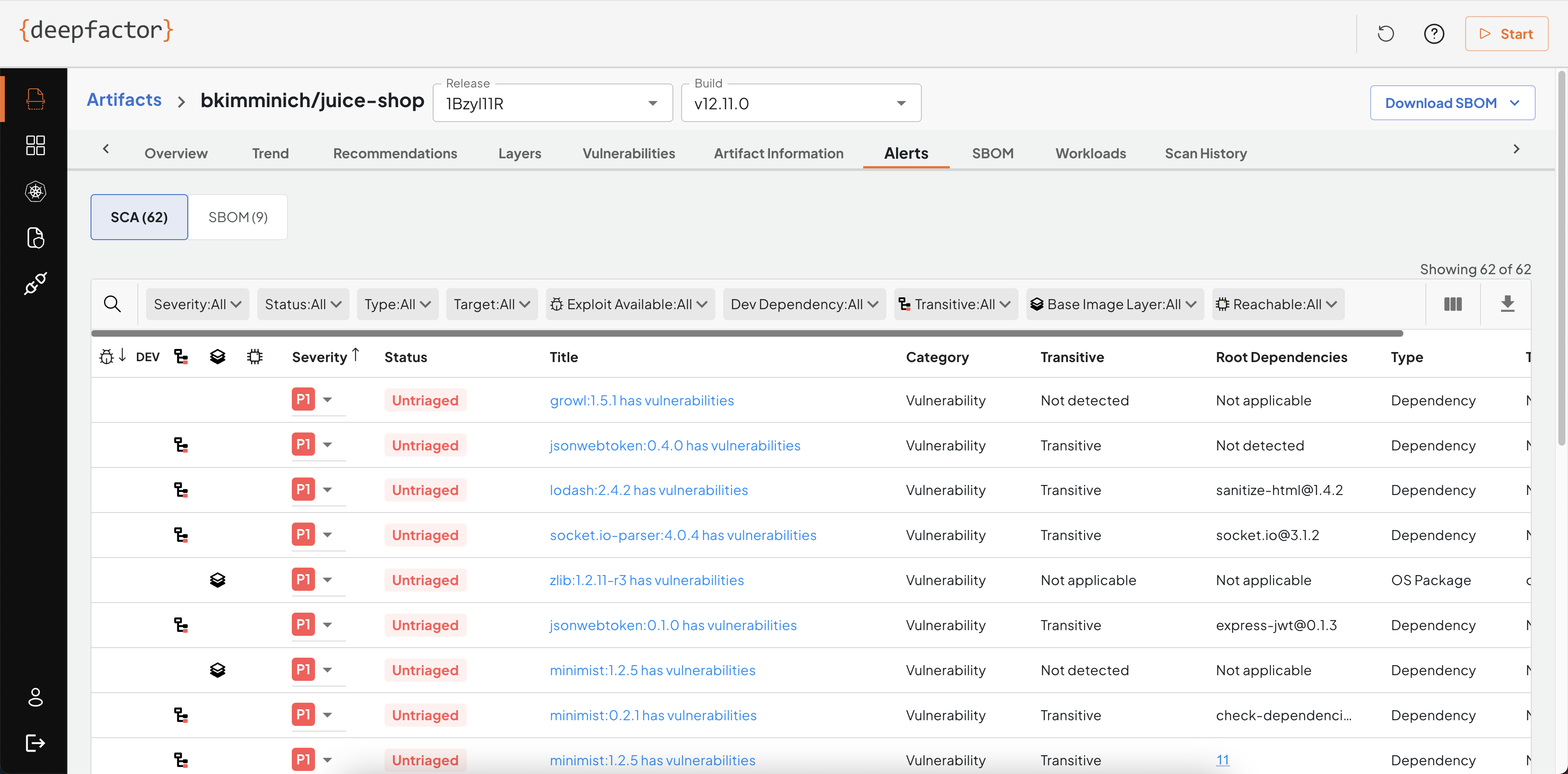
Alerts
While scanning the artifact, you can specify the policy. This tab lists all violations of policy rules.
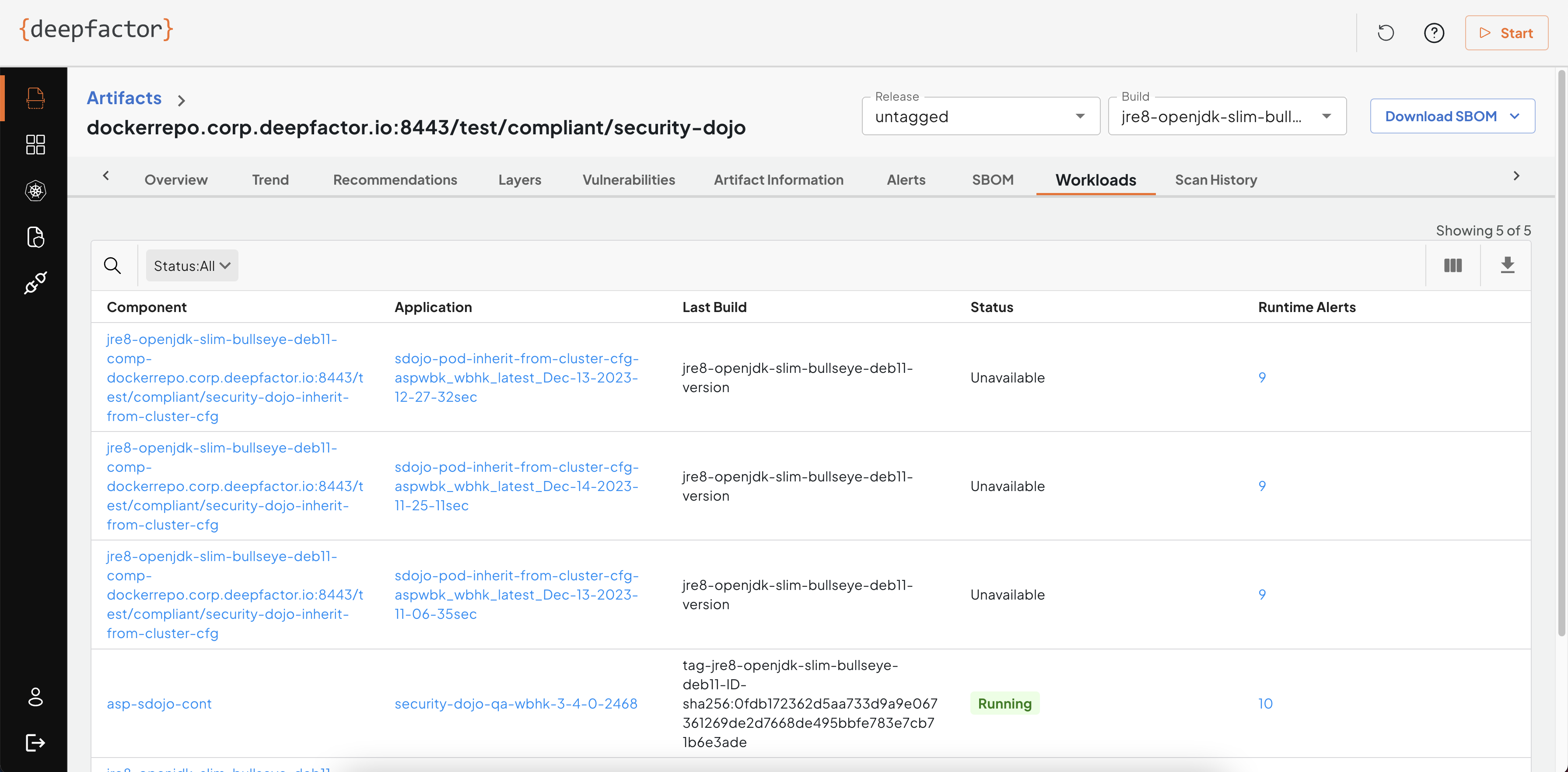
Workloads
This tab lists all of the running components that use the same artifact. This gives you visibility in the usage of a particular artifact (container image/source) in your deployed applications.
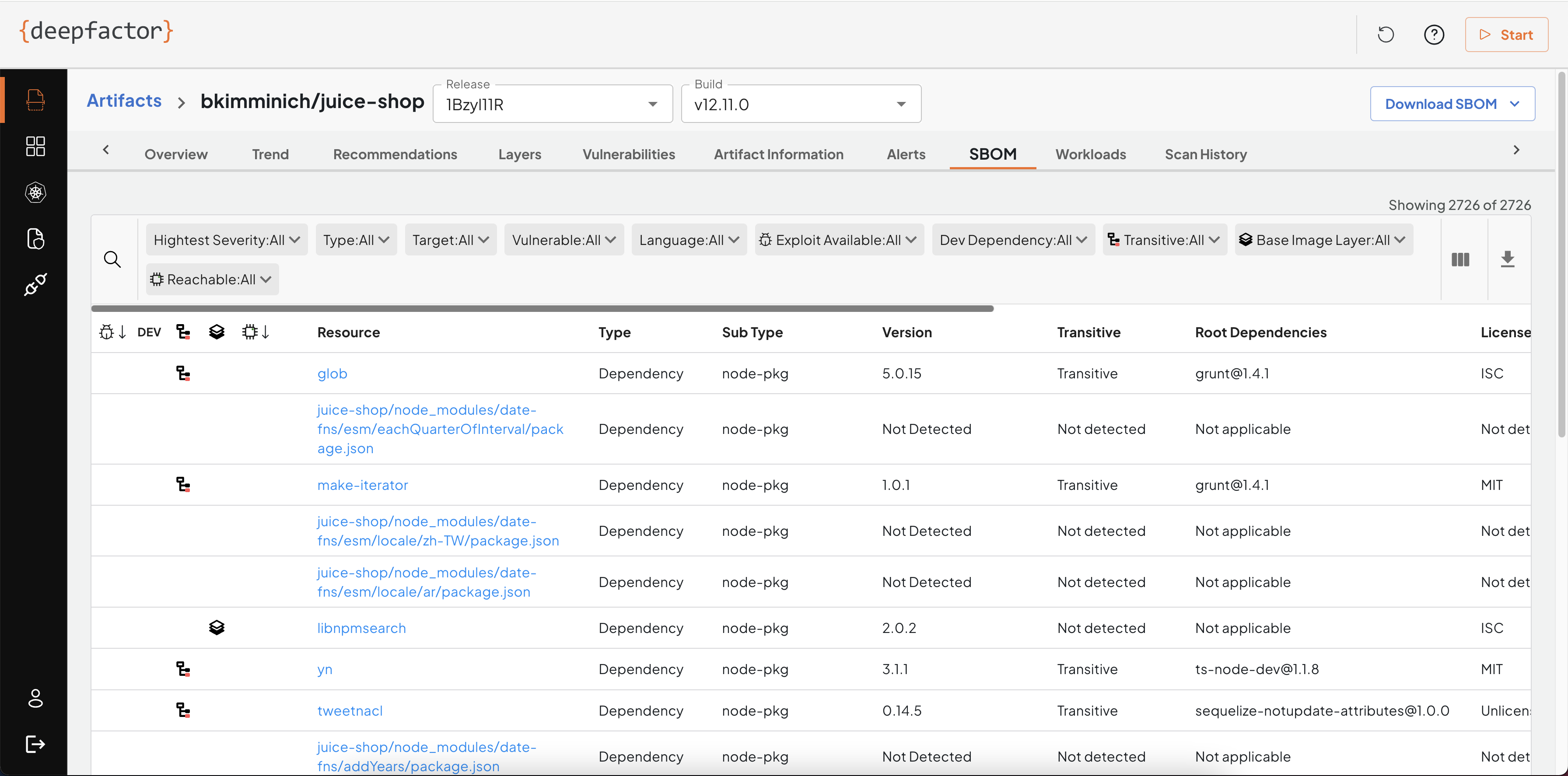
SBOM
This tab lists all resources (OS packages and dependencies) detected in your artifact along with any vulnerabilities and alerts associated with them.
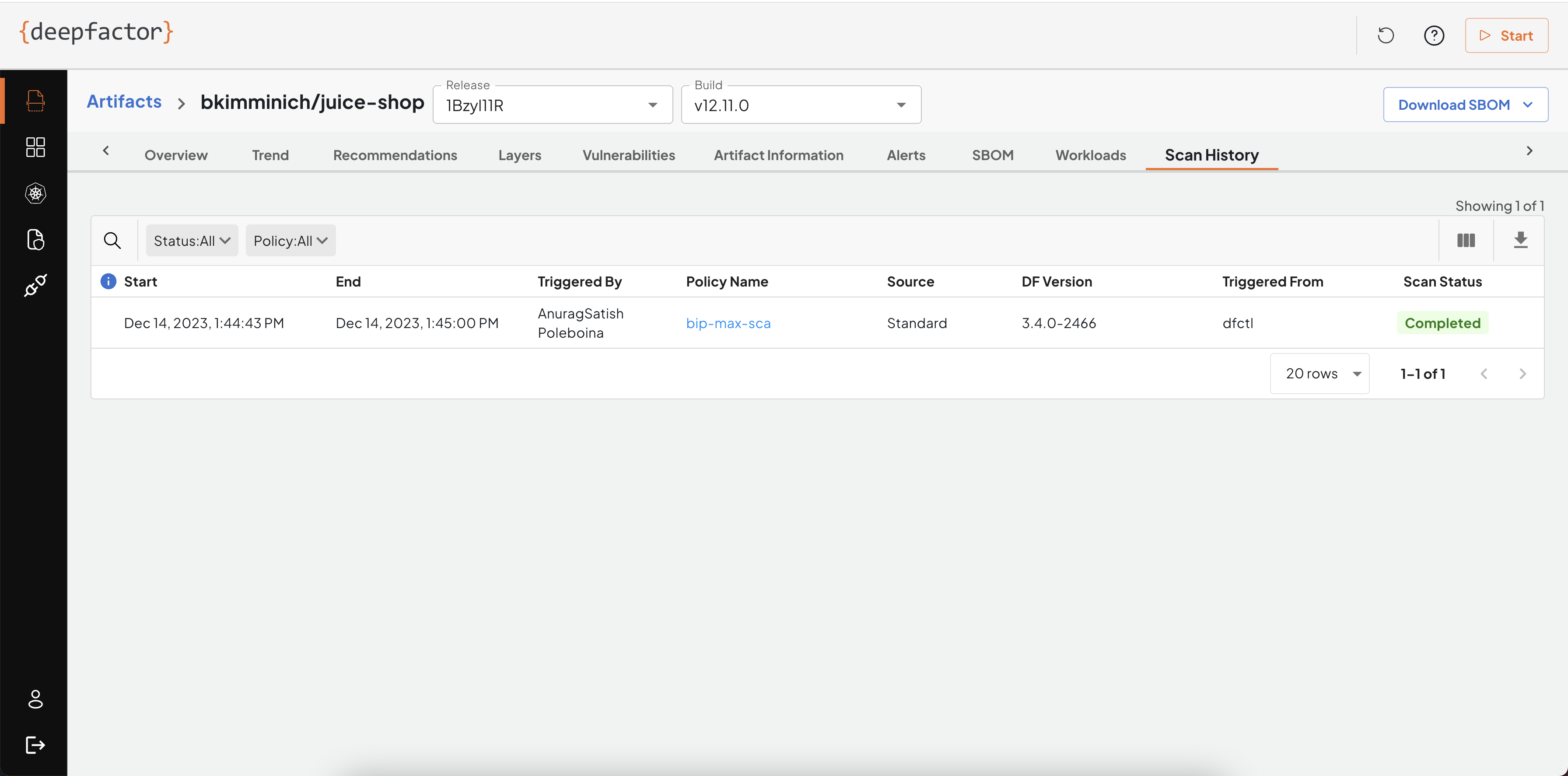
Scan History
This tab shows a list of scans performed for this particular artifact.