Introduction #
Deepfactor allows you to tag scans to a particular release of your software artifact. Software teams generally generate several builds per day in their CI/CD pipeline. Once integrated in the CI/CD pipeline or K8s cluster, Deepfactor will scan every build. However, it becomes a tedious task to go through the scan results of all of these builds and teams generally care about the latest state of their release build and want to answer the following questions:
- What is the security posture of the artifact build that is currently running in production?
- What is the security posture of the latest build of the upcoming release which is under development?
- What is the trend of vulnerabilities within a release? Are my developers reducing the vulnerability count on a per release basis?
- What is the trend of vulnerabilities across releases? Over a period of time, has the security posture for an artifact improved or has it gotten worse?
In order to help teams answer the above questions, Deepfactor has introduced the capability for users to tag a certain scan as belonging to a certain release. Once the user specifies the release for scans, Deepfactor shows the trend of vulnerabilities across builds within a single release and across the releases over a period of time.
How to tag scans to a release #
For CLI scans #
If you are scanning using the CLI or if you have integrated Deepfactor scanner in your CI/CD pipeline, you can pass the -R “release-tag” option as described in the following article
Scanning your artifacts with dfctl
For Kubernetes scan pod #
If you have installed Deepfactor helm charts in your K8s clusters, Deepfactor will install a static scan pod which automatically scans the container images for every new pod that comes in the enabled namespaces. Deepfactor can extract for the release tag from the pod spec based on your configuration. The following options are provided for you to configure how Deepfactor should extract the release tag.
- Release source: This option specifies which attribute of the pod spec should be used for extracting the release tag. Allowed options are Image Tag, label and annotation. It is a general practice to add the release string in the image tag. For example, if the release name is “3.0.1” and build number is “3301”, then image tag is generally “3.0.1-3301”.
- Release source key: If you selected label or annotation for release source, you will need to specify the name of the label or annotation whose value should be used by Deepfactor to extract the release name.
- Release scheme: Deepfactor can use the full value (image tag, label or annotation value) or it can use a regex to extract the release name from the release source.
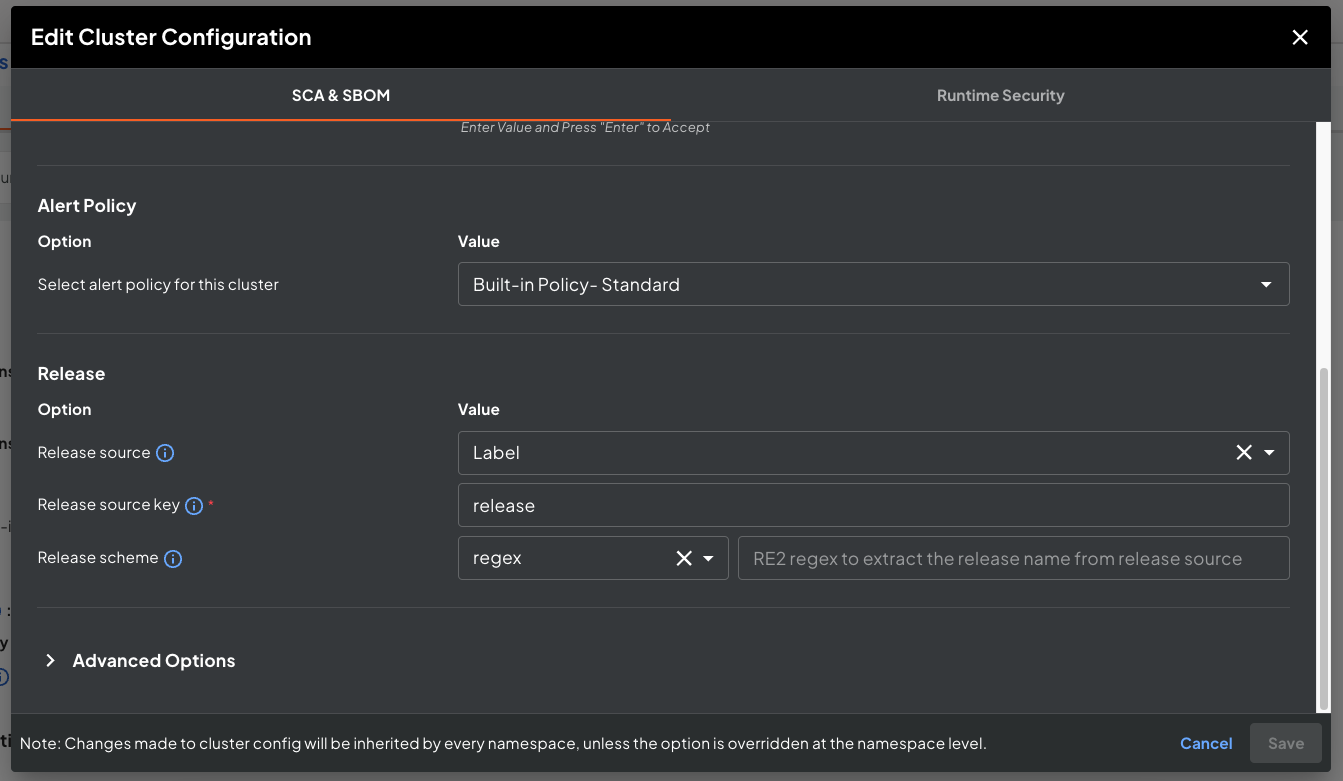
Artifact releases UI #
Trend of vulnerabilities for a single release #
Once you start tagging scans to a release, you can view the trend of vulnerabilities for a particular release. This view helps AppSec teams and developers track the progress the team is making to improve the security posture of the artifact in a particular release.
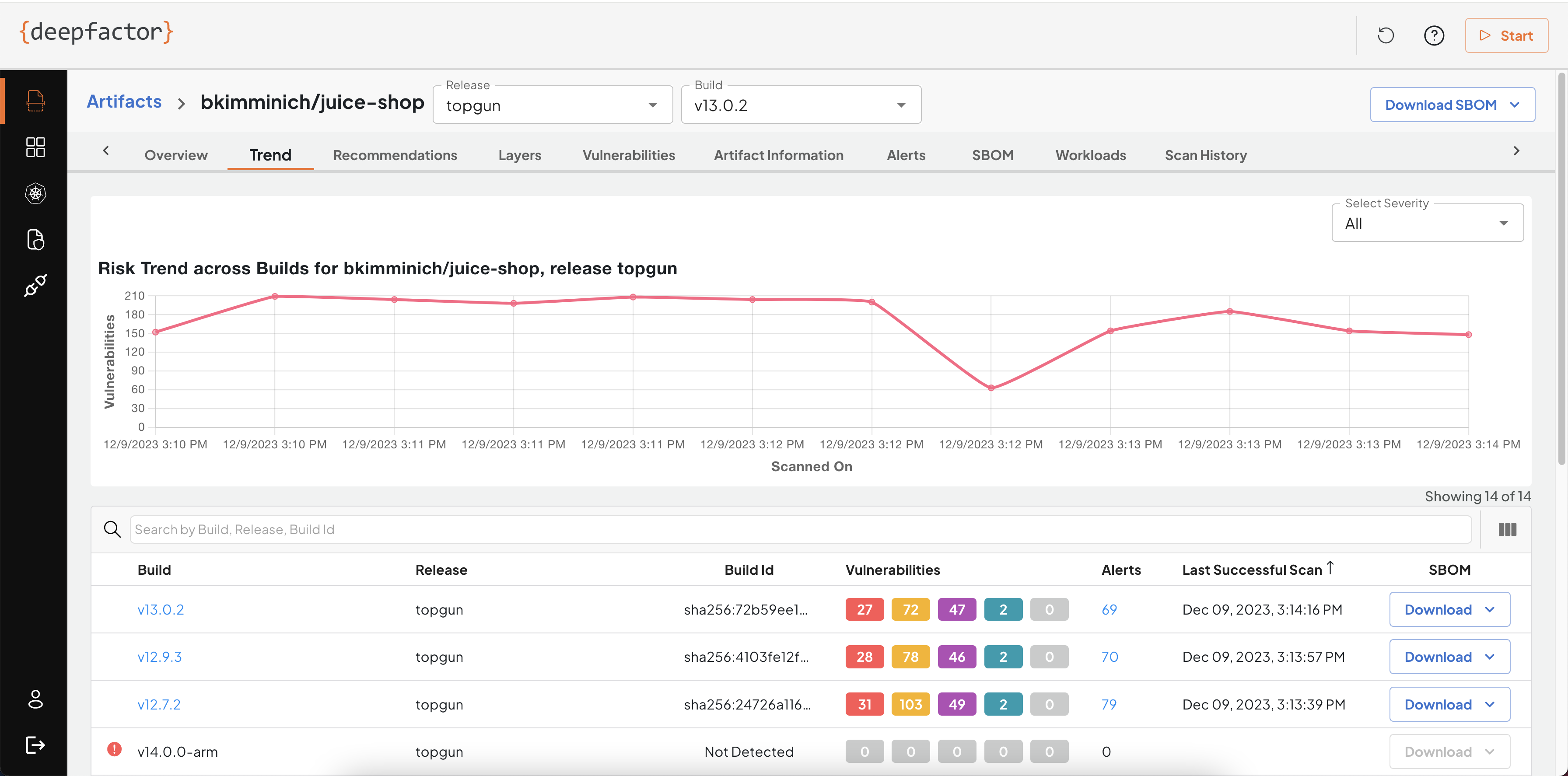
Trend of vulnerabilities across releases #
Deepfactor also shows the trend of vulnerabilities across different releases of the artifact. This view helps AppSec teams and developers track the progress the team is making to improve the security posture of the artifact across a longer period of time. This view is also a good visualization to showcase the results of the work put in by AppSec teams and developers in reducing the vulnerabilities in the artifact.
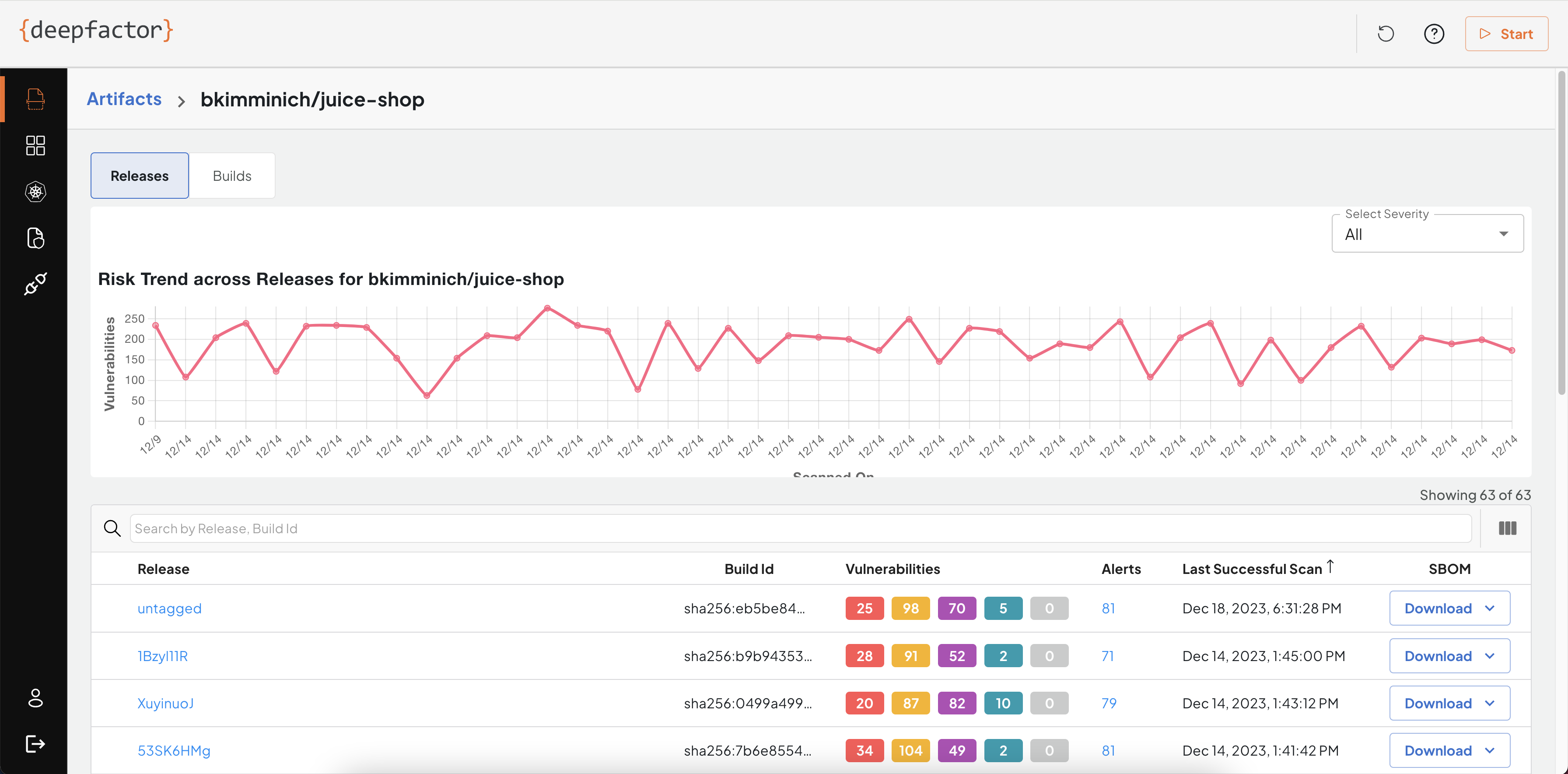
#
Untagged scans #
If you do not specify the release during a scan, Deepfactor will add all such scans to an untagged release. We strongly recommend you pass the release name during the scan as you will be able to see the trend of vulnerabilities across builds within a release and also across different releases of the artifact.

