When I first joined Deepfactor, I set out to learn as much as I could about the relevant markets and technology categories to inform our go-to-market strategy. One of the first questions I asked myself was “What category does Deepfactor fit into and what are the trends that are shaping that category?”
As an innovative new company that was built to help developers create secure cloud native applications, the first thought that came to mind was application security testing (AST). However, the vendors and tools in the AST category were designed before cloud native apps or Kubernetes existed and are still primarily used for traditional monolithic applications.
After some research, discussions with industry analysts, and conversations with Deepfactor customers, it was clear that Deepfactor was more aligned with the principles and philosophy embodied by the emerging category called Cloud Native Application Protection Platform (CNAPP). In this blog, I’ll share my research on the category, trends that are shaping the market, and thoughts on how the category will evolve over time.
History, Definition, and Business Impact
The CNAPP category first emerged in the 2021 Gartner® Hype Cycle™ for Cloud Security, where CNAPP was defined as follows:
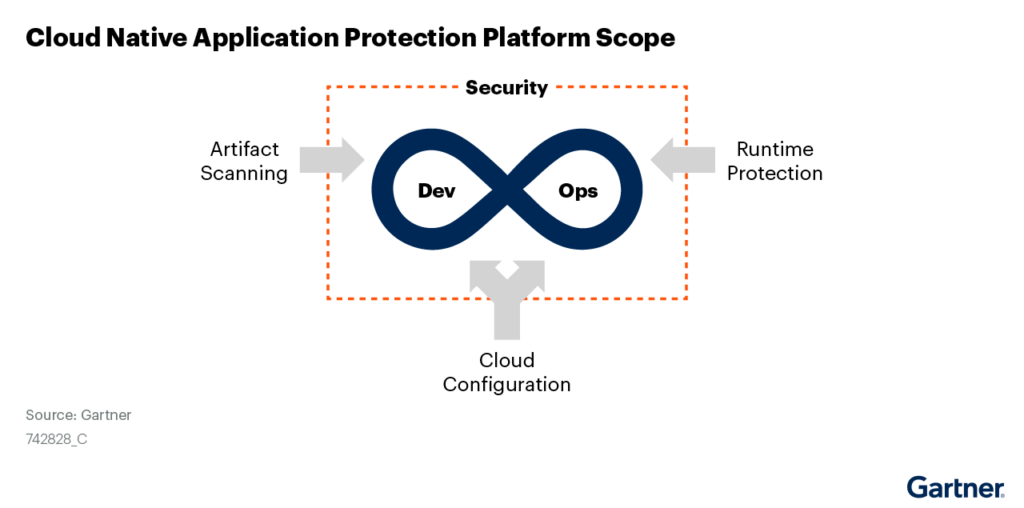
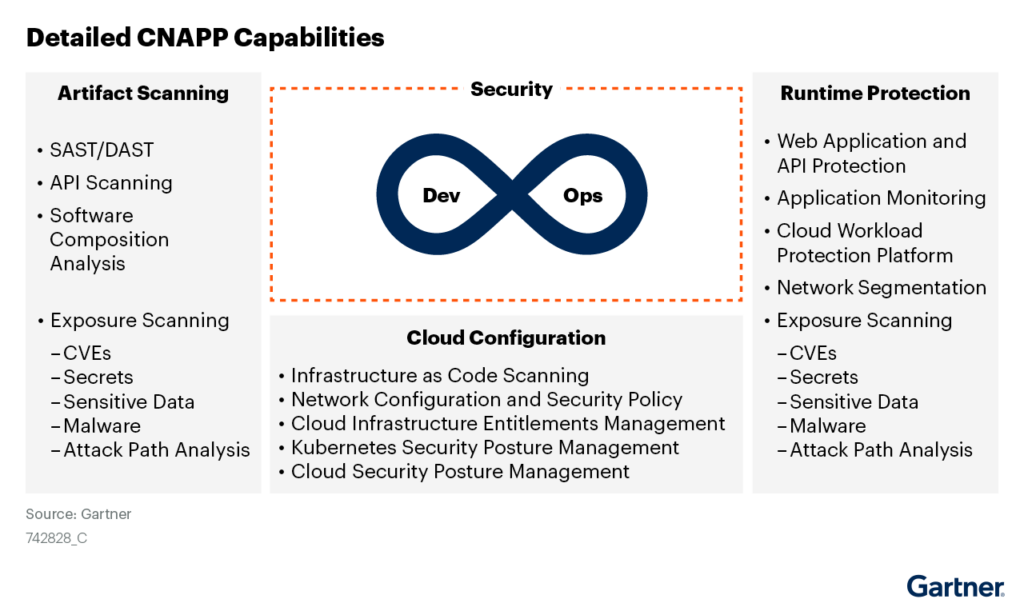
“Cloud-native application protection platforms (CNAPPs) are an integrated set of security and compliance capabilities designed to help secure and protect cloud-native applications across development and production. CNAPPs consolidate a large number of previously siloed capabilities, including container scanning, cloud security posture management, infrastructure as code scanning, cloud infrastructure entitlements management and runtime cloud workload protection platforms.”1
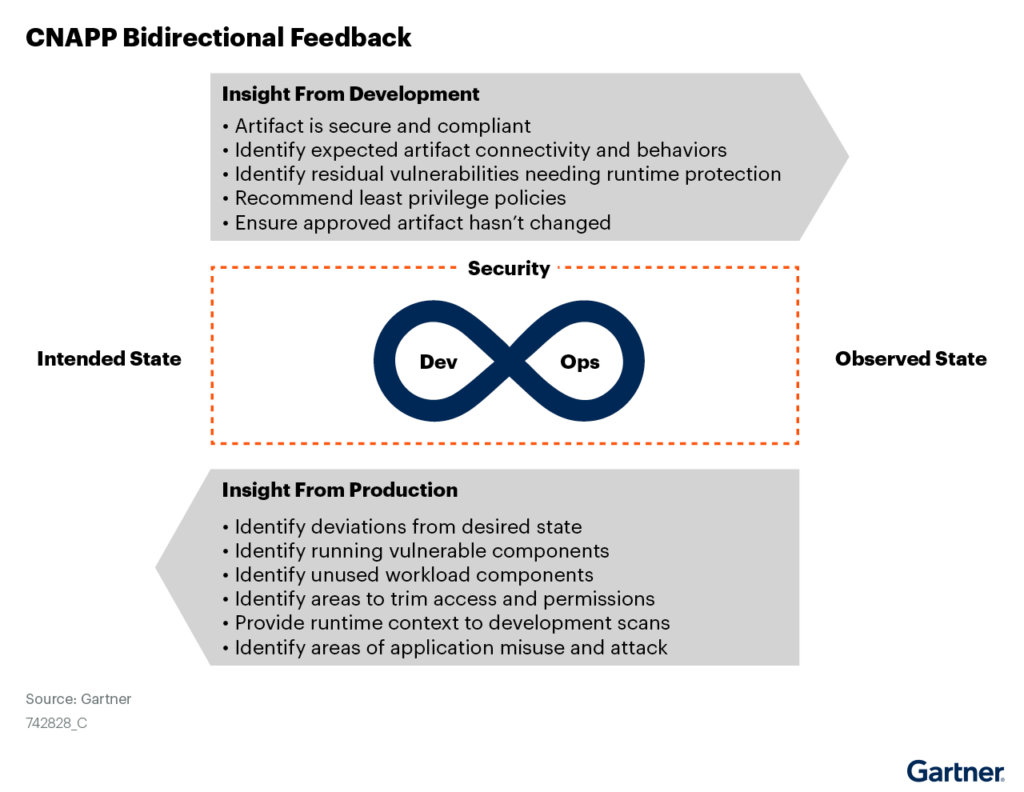
Building on the concepts and principles of DevSecOps, the vision of CNAPP is to address cloud native application security risks as much as possible in the development and testing phases of the SDLC before applications go into production. This is accomplished by providing developers with a consolidated view of cloud native application security risks and the information they need to fix known vulnerabilities, misconfigurations, behavior violations, and compliance issues in their own tools and CI/CD pipeline. By shifting security left to development, businesses that embrace CNAPP will be able to reduce the risk of breaches and regulatory penalties, lower the total cost of fixing vulnerable applications, and help engineering teams deliver secure cloud native applications faster.
Three Trends Shaping the CNAPP Category
“Properly Implemented, Cloud-Native Applications Will Be the Most Secure Applications Your Organization Has Ever Developed and Deployed. But You Must Discard the Baggage of Your Conventional Thinking, Tools and Processes for Security.”2
1. The Speed of Software Development
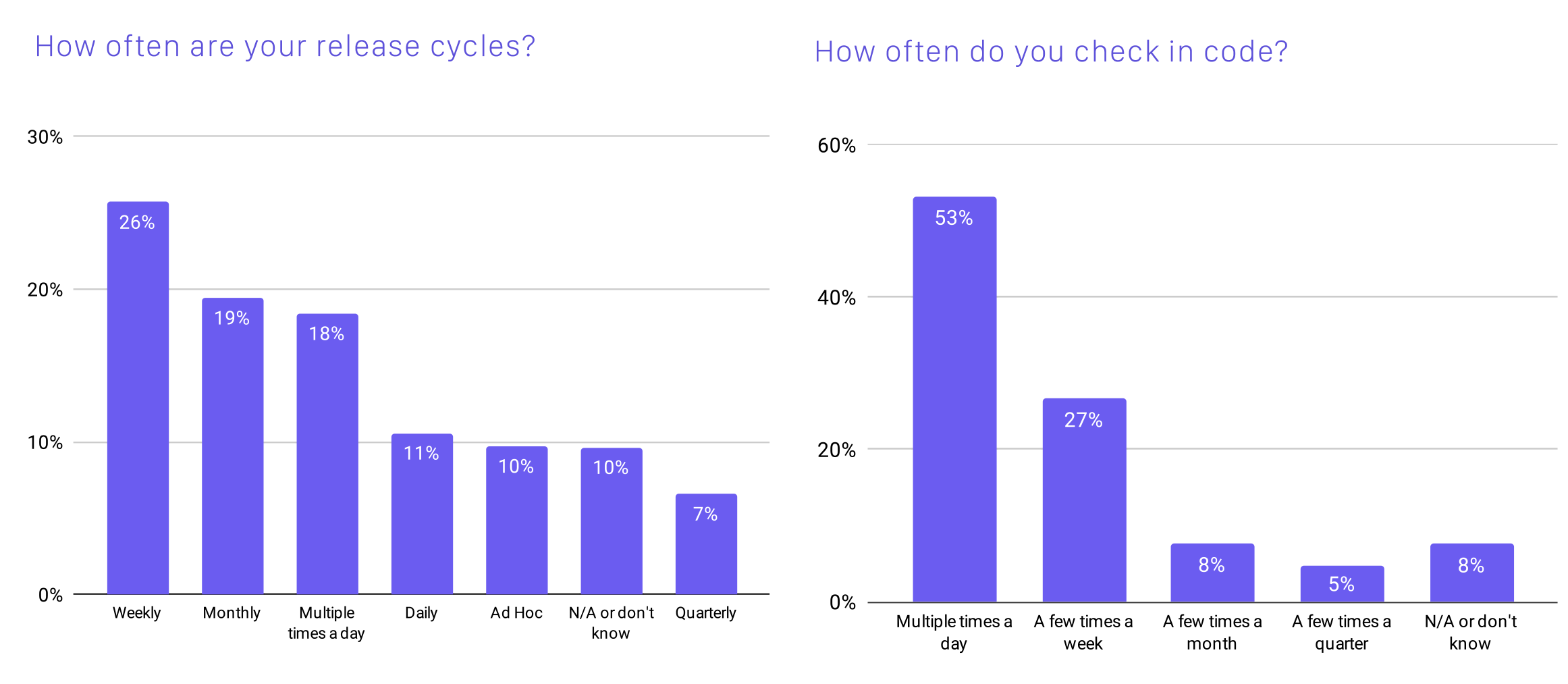
Digital transformation, cloud native applications, containers, Kubernetes, and agile development practices have accelerated release frequency and complexity, making it challenging to address security risks without slowing down development. According to the Cloud Native Computing Foundation (CNCF) Survey, 55% of respondents release code weekly or more frequently, with 18% releasing multiple times per day. Additionally, 53% of respondents said that they check in code multiple times per day. With daily and weekly releases, using a traditional application security approach that gates releases before going into production for security testing negates many of the speed and agility benefits realized by digital transformation.
Source: Cloud Native Cloud Computing Foundation Survey
2. DevSecOps—Shifting Left To Address Security in Development
DevSecOps, or the concept of “Shifting Left,” refers to moving as much application security testing to the “Dev” side of “DevOps” as possible. The underlying premise is that it is faster, cheaper, and easier to catch as many vulnerabilities, risks, and compliance issues as possible in development and test before code is shipped to production. In the context of CNAPP, shifting left means addressing the following application security checks in development and test:
- Artifact scanning (SAST/DAST, API Scanning, Software Composition Analysis, Known Vulnerabilities) to eliminate known application risks
- Cloud configuration management to avoid misconfigurations that could lead to a breach
- Runtime behavior analysis to ensure your application isn’t exposing data or mining crypto
- Compliance checks to validate that you aren’t violating any relevant compliance regulations (PCI, SOC2…
3. The Growing Business Impact of Security Incidents
The business impact of security incidents such as data breaches, zero day vulnerabilities, and privacy violations continue to grow, making it a necessity to treat security as a critical part of digital transformations and cloud native application development. Whether you are Solar Winds, Zoom, or any one of a number of other companies affected by data breaches, the stakes are high with consequences ranging from lost customers to bankruptcy. The average data breach costs businesses in the United States $9.05 Million3, the Log4j zero day vulnerability is affecting hundreds of millions4 of apps and devices, and data privacy regulations have resulted in fines of $888 million (USD)5. The costs of neglecting security and compliance in the development process continue to rise over time, making it imperative that businesses undergoing digital transformation or building new cloud apps create a repeatable and sustainable process to find and resolve application vulnerabilities early in that development process rather than paying the price in production.
The Future of Cloud and AppSec
While CNAPP is the name of a new emerging category, it is also at the future of the three existing multi-billion markets that are converging: Application Security Testing (AST—$2.6B), Cloud Workload Protection Platforms (CWPP—$2.44B), and Cloud Security Posture Management. In addition, venture capitalists funded 62 new companies with $1.34B from 2019-2020, including Deepfactor.
With this level of investment from both existing companies and innovation from new funded venture-based startup companies, CNAPP will be at the center of both cloud and application security for the next 5-10 years.
“By integrating vulnerabilities, context and relationships across the development life cycle, excessive risk can be surfaced, enabling development teams and product owners to focus on remediating the areas of the application that represent the most risk.”6
The behavior, usage, and context of the application observed in runtime helps prioritize security risks to fix in development, while artifact scanning for known vulnerabilities, dependencies, and secure building blocks of code help inform where additional protective security controls are required.
Today, existing CWPP solutions are trying to shift left to integrate their runtime knowledge from production to inform secure development, AST solutions as trying to retrofit their solutions to address cloud native application development methodologies, and CSPM vendors are trying to move beyond configuration management to add protection and artifact scanning capabilities. New companies like Deepfactor are starting left in development and designing innovative solutions focused on helping developers find and resolve vulnerabilities early in development and test.
As I observe more customers going through the CNAPP journey, I plan to continue sharing what I learn in the form of additional blogs on the topic. I look forward to watching the CNAPP category and Deepfactor grow over the coming years by helping developers secure their cloud native applications.
[1] Gartner, “Hype Cycle for Cloud Security, 2021”, 27 July 2021, Tom Croll, Jay Heiser. GARTNER and HYPE CYCLE are a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and are used herein with permission
[2] Gartner, 2021 Security and Risk Summit Presentation, Best Practices for Securing Cloud-Native Application Build on Containers and Kubernetes Neil MacDonald, 18 of November, 2021
[3] IBM Ponemon Institute Cost of a Data Breach Report 2021