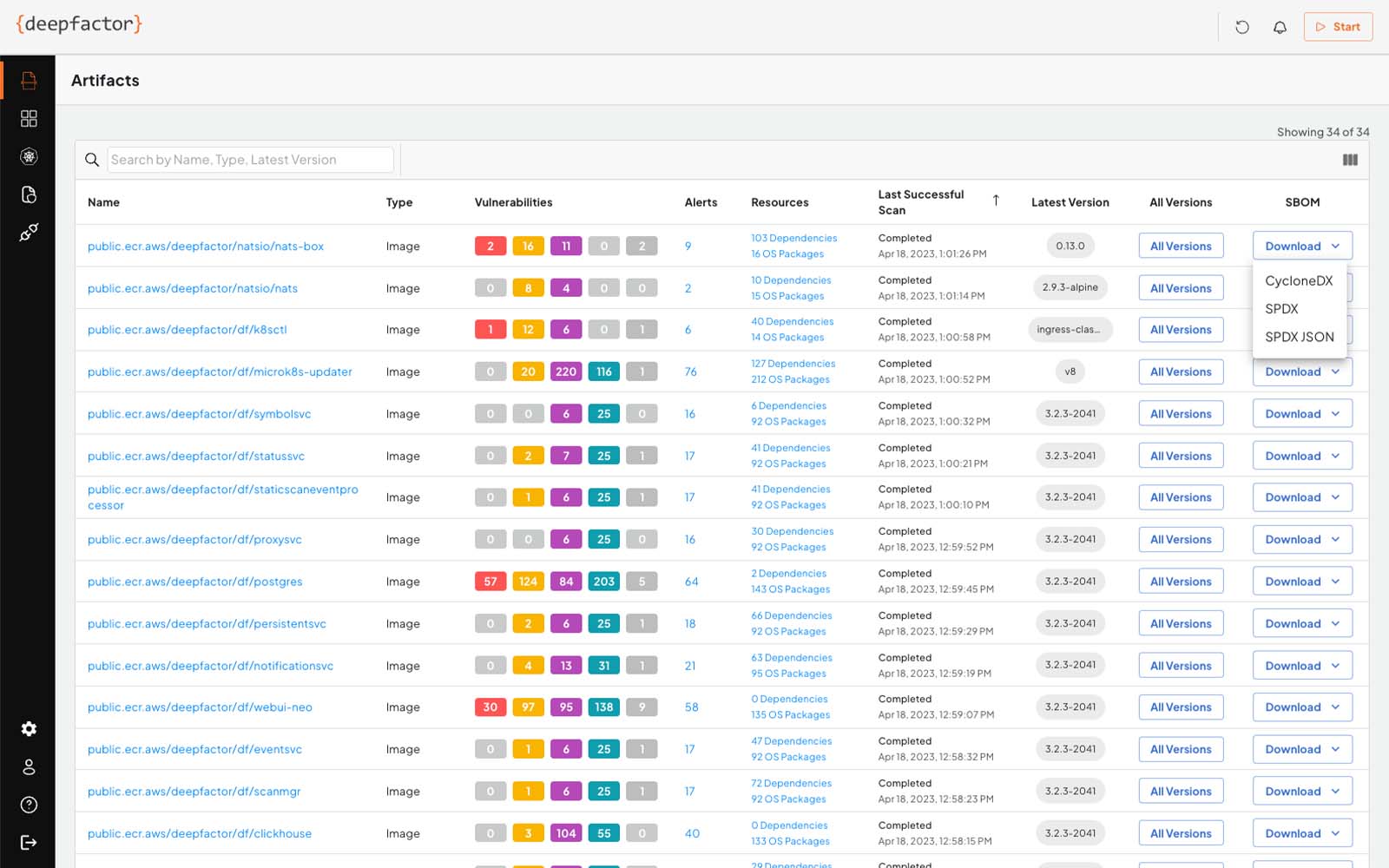

Software Bill of Materials (SBOM)
Deepfactor generates software bills of materials (SBOMs) in CycloneDX and SPDX formats to help businesses that develop software automatically create and manage SBOMs as part of their Software Development Lifecycle (SDLC). These capabilities will enable businesses to improve supply chain security and comply with requirements set by the U.S. Federal Government.
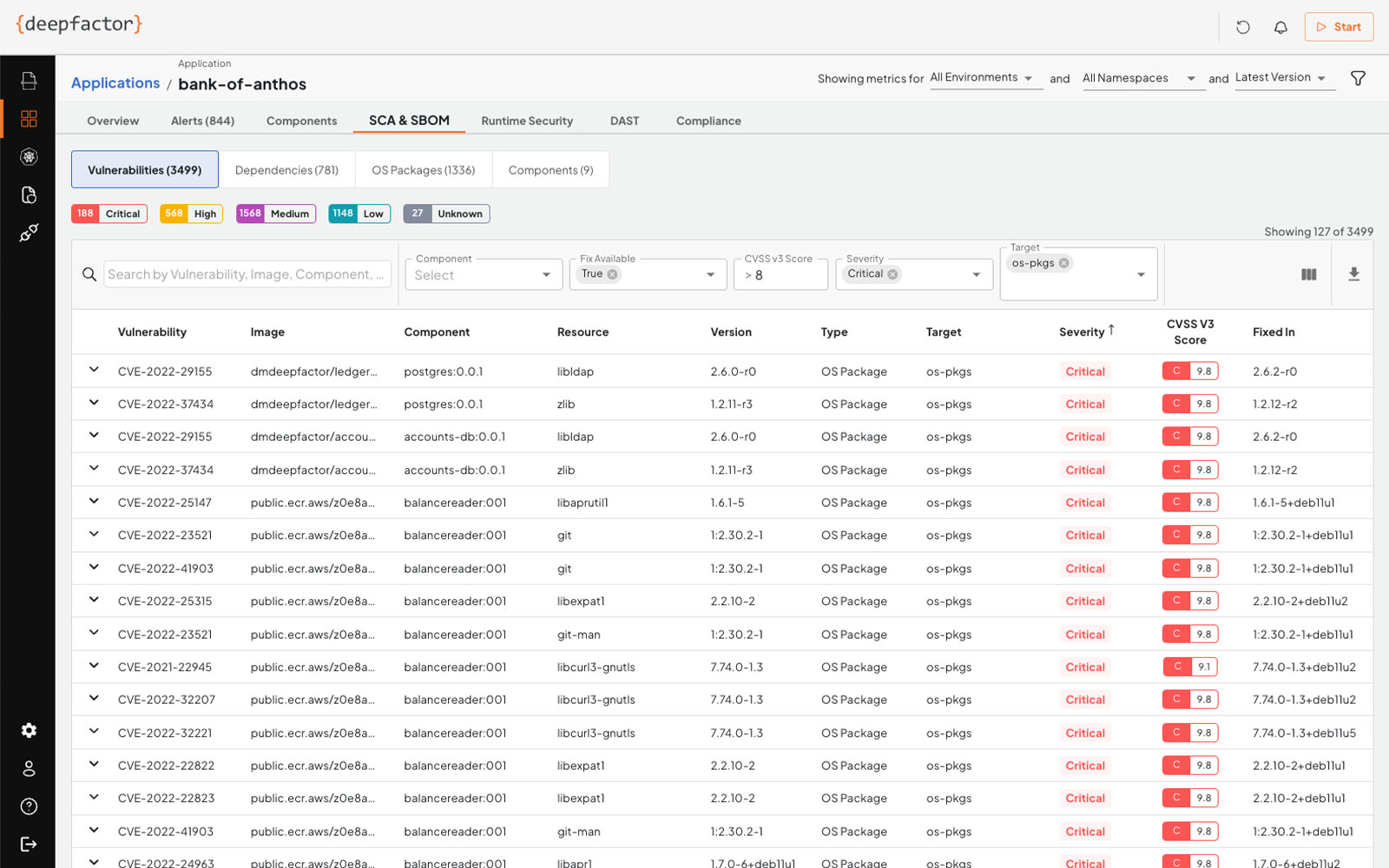

Software Composition Analysis (SCA)
Deepfactor scans containers, open source software, OS packages, and dependencies for CVEs and provides the ability to gate builds and pull requests if Deepfactor detects critical vulnerabilities. Deepfactor performs a scan of containers, OS packages, and images to analyze them against over a dozen publicly available vulnerability databases (such as the NIST Vulnerability Database).
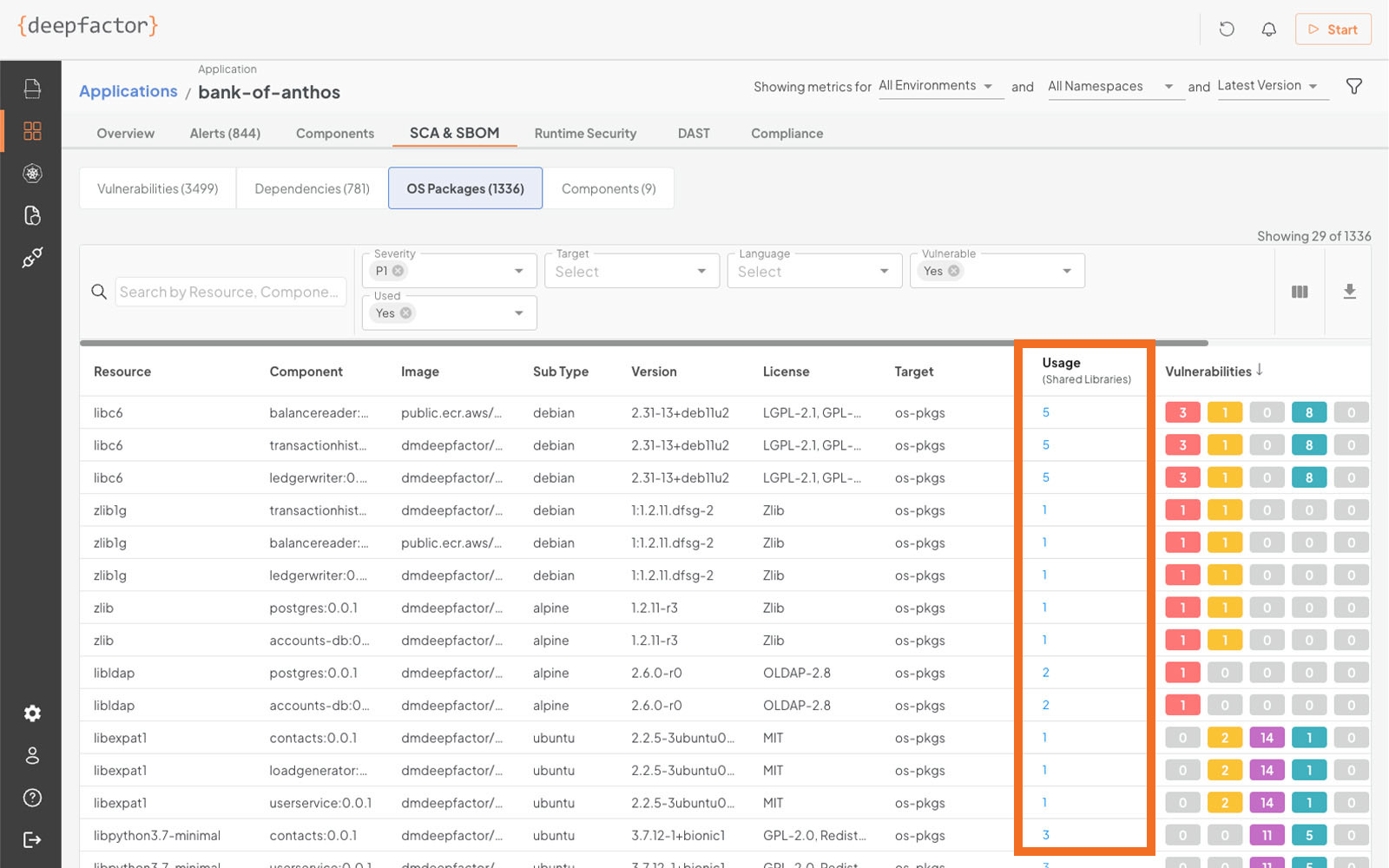

Runtime SCA
Unlike traditional static Software Composition Analysis (SCA) tools, Deepfactor Runtime SCA correlates static SCA findings with runtime usage behavior to filter and prioritize vulnerability alerts. The Deepfactor correlation engine observes the application while it’s running in test, dev, staging, or production environments to determine whether vulnerable dependencies and packages are used during the application runtime, providing valuable context that accelerates remediation of vulnerabilities and provides guidance on slimming down unused components.
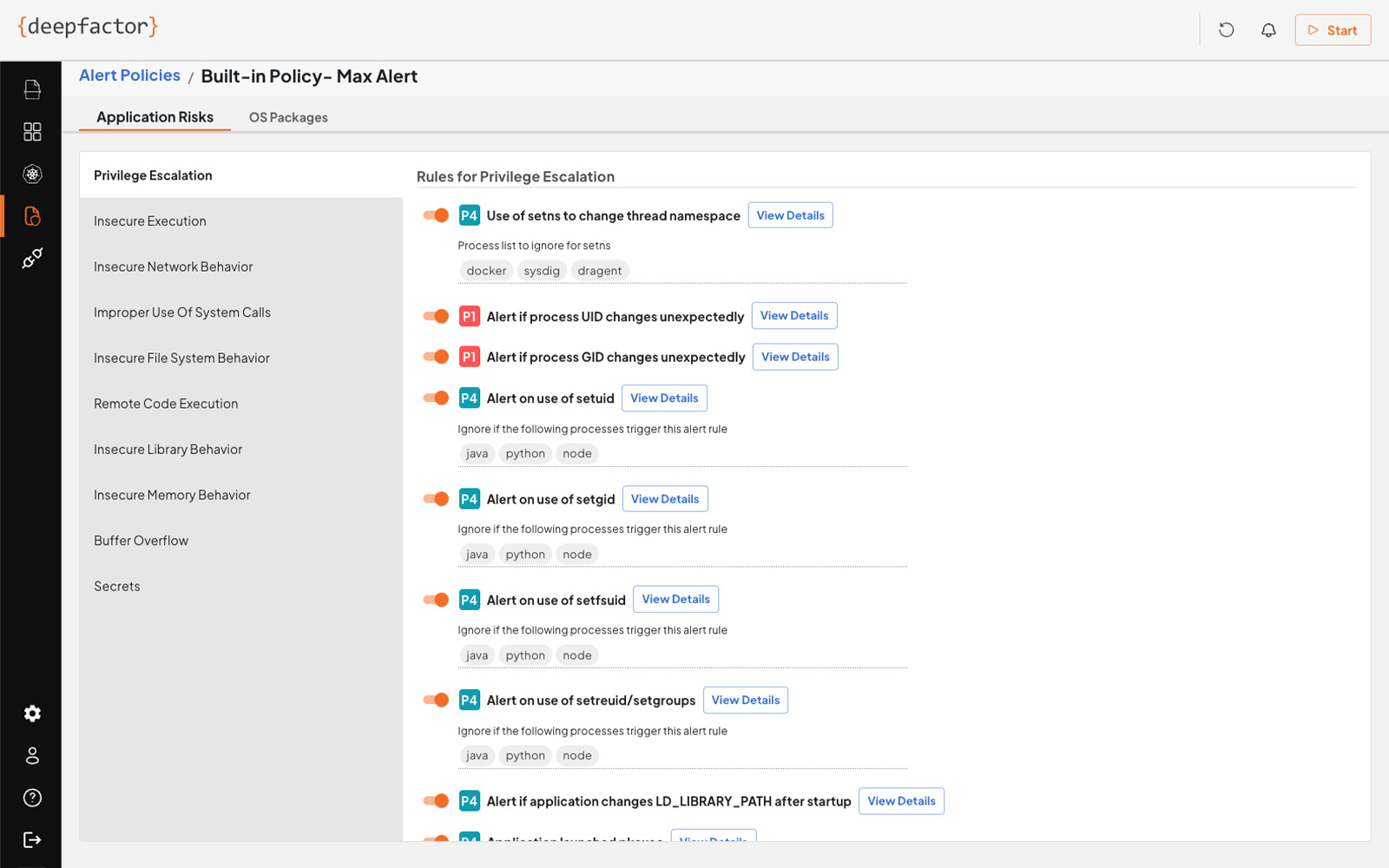

Runtime Analysis
Deepfactor identifies unknown vulnerabilities by analyzing running applications in the development and test environments before releasing code to production. Based on deep visibility of every thread and process, Deepfactor can detect application risks based on customizable policies that monitor for vulnerabilities such as insecure execution, file system behavior, remote code execution, and buffer overflows that can lead to data breaches or be used by zero day attacks.
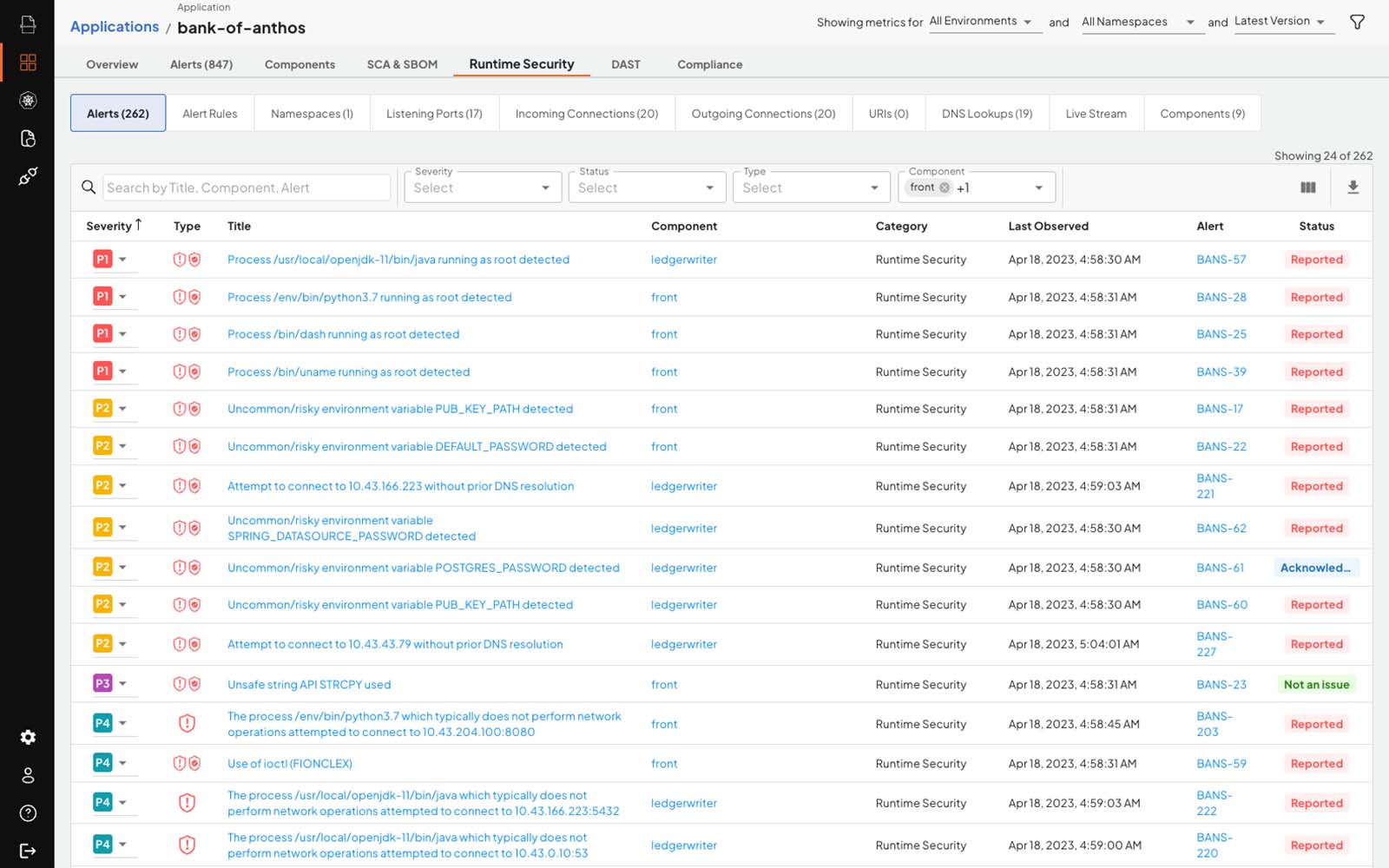

Container Runtime Security
Deepfactor Container Runtime Security monitors applications in production environments to detect runtime security risks in filesystem, network, process, and memory behavior including exposing sensitive information, privilege escalation, and prohibited network communications. Runtime security in production environments helps demonstrate compliance (SOC 2, etc.) and uncovers indicators of compromise by pinpointing suspicious file, network, and memory behaviors.
Detect Security Risks Before Shipping
Deepfactor observes running applications in development and testing to help engineering teams uncover critical security risks in custom and third-party code.
Provide Contextual and Actionable Alerts
Deepfactor generates prioritized insights that enable developers to pinpoint insecure code, streamline remediation, analyze drift between releases, and understand potential impact to compliance objectives.
Generate a Dynamic Bill of Materials
Deepfactor distinguishes between active and inactive code, and collects valuable information about the application including packages, dependencies, licenses, processes, and network connections.
14-DAY FREE TRIAL
Deepfactor SaaS includes the full functionality of the Deepfactor Developer Security platform hosted in a multi-tenant environment.
Sign Up Today!Purpose-Built To {Observe} Cloud Native Applications
With a single command Deepfactor seamlessly loads a robust language-agnostic library into cloud native workloads and environments.
NO Agents. NO Sidecars. NO Kernel Modules.
$ helm install df-webhook deepfactor/webhook -f override.yaml_
$ dfctl run –a “MyApp” –c “MyService” --docker-run --image myservice:latest_
$ dfctl scan deepfactor/my-service:tag1234
Use Cases
DevSecOps >
Supply Chain Security >
Compliance >
Cloud Native Application Security >
Software Bill of Materials >
Developer Security Starts Here
75%
75%
75%
Reduce Security Risks
Find 75% more security vulnerabilities in development before shipping to production than with traditional security tools.
90%
90%
90%
Accelerate Release Cycles
Eliminate 90% of release delays due to security issues by discovering critical security risks in development and testing.
100%
100%
100%
Build a Security Culture
Teach 100% of developers secure coding by providing timely and actionable security best practices, continuously building security knowledge over time.


;)